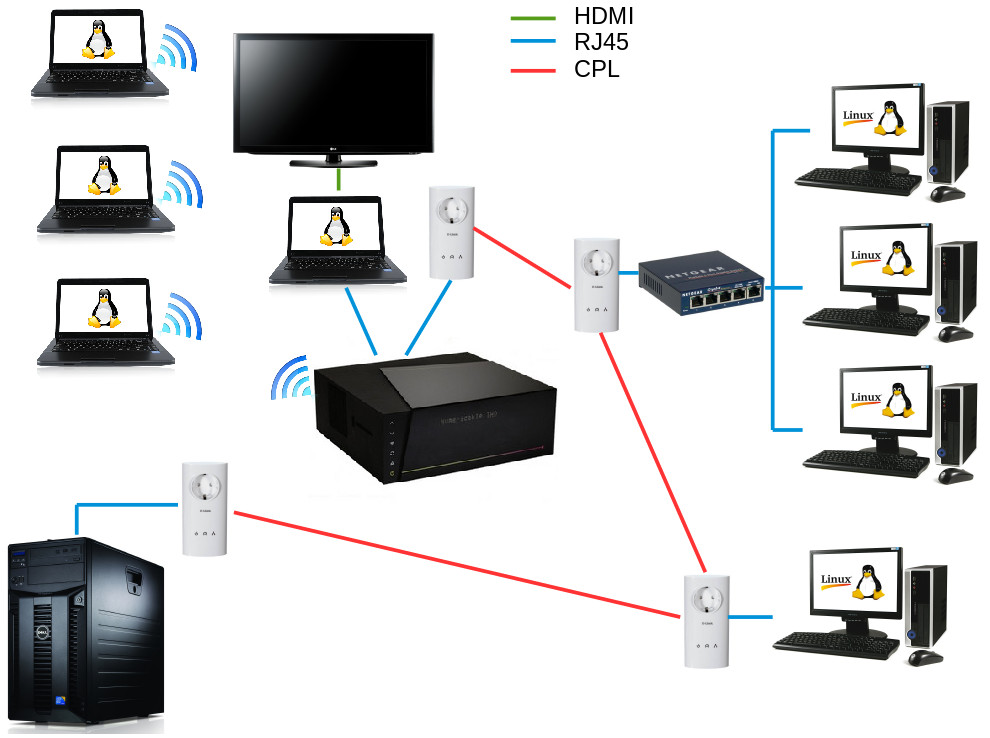
Securing your Linux workstation
Last modified September 11, 2021This site has been automatically translated with Google Translate from this original page written in french, there may be some translation errors
Presentation
Possible attacks
Presentation
User account
To avoid this, check your /etc/passwd file and delete all your generic user accounts (not system accounts!!).
Make sure that no user has no password and even less a password identical to the login (very common!!).
The "r" tools (rsh, rlogin, ...)
- rsh opens a remote shell (to launch a command for example), if you want a secure equivalent tool, turn to SSH .
- rlogin , equivalent to telnet , if a user places a .rhosts file in his homedirectory containing obelix , anyone on the obelix machine will be able to connect to his account without having to give a password. If you have a /etc/hosts.equiv containing a + , anyone will have access to your machine.
- rexecd , this is the server to accept rexec requests , allows you to launch commands remotely. The server does not log any connection failures, therefore you can try a ton of passwords without the administrator of the targeted machine noticing.
FTP
Do not run an anonymous FTP server unless you know what you are doing, be aware that FTP daemons are known to have quite a few security issues, a poorly configured FTP server can very well serve as a gateway for a hacker to attack your machine of course but also other machines.TFTP (Trivial File Transfer Protocol) is a simplified FTP service , it is used in particular for booting X terminals. It does not require any authentication, anyone can connect and read what they want.
So I advise you to disable everything that revolves around FTP and to favor SFTP provided with OpenSSH .
Stats tools
Par exemple avec systat et netstat qui tournent sur votre système, un hacker peut visualiser vos process actifs ainsi que la configuration réseau. Des outils comme rusersd et rstatd permettent à un hacker de visualiser les gens qui sont logués à un moment donné. Finger permet de connaître les logins existants sur la machine.
NFS
Web server
scripts , there are many other flaws in an HTTP server , whether it's at the level of a bad configuration, buggy servers, ... even the logs can be a problem, if they are visible from the internet, especially those containing errors (page 404), which can contain sensitive information such as user logins.
Mail server
servers , be aware that there was a bug on these servers (buffer overrun) that allowed you to launch commands as root remotely. Update them, or disable them. Some POP servers do not log login errors, so anyone can try a ton of passwords without you realizing. Finally, POP/IMAP manipulates passwords in clear text, you can very well intercept a POP request on the network (by sniffing) and recover the login and password. Prefer secure POP servers (APOP, POP3s ...).
Others
Securing your workstation
Installing the distribution
When it comes to partitioning the system, I advise you to create several partitions to properly separate the system from the data, for example:
/ 10 GB
/usr 10 GB at least
/var 5 GB
/home 10 GB per user at least
swap 2*RAM size at least
/usr/local at least 10 GB (to store your apps)
Once the installation is complete, activate the system update automatically or not, these updates correct security holes. These patches are essential to properly secure a system, if you have not activated the automatic update, you must regularly monitor their release. Be aware that there are mailing lists on this subject that will automatically notify you of the release of a new patch. Personally I have not activated the automatic update because I prefer to control the installation of packages, some of which can cause regressions, it is necessary to analyze on a case-by-case basis.
I advise you to keep an administrator's notebook where you will note each of your system manipulations, it can be a bit schoolboyish, even tedious, but it can be extremely useful in certain cases. A simple text file (400 root owner rights) with a copy and paste of the commands (and the results that go with them), and a few annotations should do the trick.
Éliminate unnecessary services
Systemd is a super daemon that allows you to launch a whole bunch of other daemons (or services) all by itself. It is based on what we call units, there are several kinds
automount : for filesystems mounted with automount
device : for devices (special files)
mount : for filesystems mounted (using /etc/fstab or on the fly (USB stick, ...)
path : for scripts and exe indicated by their path
service : for daemons
socket : for sockets
swap : for swap
target : for groups of several units (for example network.target manages all my network related services)
UNIT LOAD ACTIVE SUB DESCRIPTION
proc-sys-fs-binfmt_misc.automount loaded active waiting Arbitrary Executable File Formats File System Automount Point
sys-devices-pci0000:00-0000:00:01.0-0000:01:00.1-sound-card1.device loaded active plugged GK104 HDMI Audio Controller
sys-devices-pci0000:00-0000:00:14.0-usb3-3\x2d2-3\x2d2:1.2-sound-card2.device loaded active plugged LifeCam HD-3000
sys-devices-pci0000:00-0000:00:19.0-net-eno1.device loaded active plugged Ethernet Connection I217-V
sys-devices-pci0000:00-0000:00:1a.0-usb1-1\x2d1-1\x2d1.5-1\x2d1.5:1.0-bluetooth-hci0-rfkill0.device loaded active plugged /sys/devices/pci0000:00/0000:00:1a.0/usb1/1-1/1-1.5/1-1.5:1.0/bluetooth/hci0/rfkill0
sys-devices-pci0000:00-0000:00:1a.0-usb1-1\x2d1-1\x2d1.5-1\x2d1.5:1.0-bluetooth-hci0.device loaded active plugged /sys/devices/pci0000:00/0000:00:1a.0/usb1/1-1/1-1.5/1-1.5:1.0/bluetooth/hci0
sys-devices-pci0000:00-0000:00:1b.0-sound-card0.device loaded active plugged 8 Series/C220 Series Chipset High Definition Audio Controller
sys-devices-pci0000:00-0000:00:1c.7-0000:03:00.0-ieee80211-phy0-rfkill1.device loaded active plugged /sys/devices/pci0000:00/0000:00:1c.7/0000:03:00.0/ieee80211/phy0/rfkill1
sys-devices-pci0000:00-0000:00:1c.7-0000:03:00.0-net-wlp3s0.device loaded active plugged RTL8821AE 802.11ac PCIe Wireless Network Adapter
sys-devices-pci0000:00-0000:00:1f.2-ata1-host0-target0:0:0-0:0:0:0-block-sda-sda1.device loaded active plugged LITEON_IT_LMT-256L9M 1
sys-devices-pci0000:00-0000:00:1f.2-ata1-host0-target0:0:0-0:0:0:0-block-sda-sda2.device loaded active plugged LITEON_IT_LMT-256L9M 2
sys-devices-pci0000:00-0000:00:1f.2-ata1-host0-target0:0:0-0:0:0:0-block-sda-sda3.device loaded active plugged LITEON_IT_LMT-256L9M 3
sys-devices-pci0000:00-0000:00:1f.2-ata1-host0-target0:0:0-0:0:0:0-block-sda-sda4.device loaded active plugged LITEON_IT_LMT-256L9M 4
sys-devices-pci0000:00-0000:00:1f.2-ata1-host0-target0:0:0-0:0:0:0-block-sda-sda5.device loaded active plugged LITEON_IT_LMT-256L9M 5
sys-devices-pci0000:00-0000:00:1f.2-ata1-host0-target0:0:0-0:0:0:0-block-sda-sda6.device loaded active plugged LITEON_IT_LMT-256L9M 6
sys-devices-pci0000:00-0000:00:1f.2-ata1-host0-target0:0:0-0:0:0:0-block-sda.device loaded active plugged LITEON_IT_LMT-256L9M
sys-devices-pci0000:00-0000:00:1f.2-ata2-host1-target1:0:0-1:0:0:0-block-sdb-sdb1.device loaded active plugged WDC_WD10EZEX-21M2NA0 1
sys-devices-pci0000:00-0000:00:1f.2-ata2-host1-target1:0:0-1:0:0:0-block-sdb.device loaded active plugged WDC_WD10EZEX-21M2NA0
sys-devices-pci0000:00-0000:00:1f.2-ata4-host3-target3:0:0-3:0:0:0-block-sr0.device loaded active plugged MATSHITADVD-RAM_UJ8E0
sys-devices-platform-serial8250-tty-ttyS0.device loaded active plugged /sys/devices/platform/serial8250/tty/ttyS0
sys-devices-platform-serial8250-tty-ttyS1.device loaded active plugged /sys/devices/platform/serial8250/tty/ttyS1
sys-devices-platform-serial8250-tty-ttyS2.device loaded active plugged /sys/devices/platform/serial8250/tty/ttyS2
sys-devices-platform-serial8250-tty-ttyS3.device loaded active plugged /sys/devices/platform/serial8250/tty/ttyS3
sys-subsystem-bluetooth-devices-hci0.device loaded active plugged /sys/subsystem/bluetooth/devices/hci0
sys-subsystem-net-devices-eno1.device loaded active plugged Ethernet Connection I217-V
sys-subsystem-net-devices-wlp3s0.device loaded active plugged RTL8821AE 802.11ac PCIe Wireless Network Adapter
-.mount loaded active mounted /
dev-hugepages.mount loaded active mounted Huge Pages File System
dev-mqueue.mount loaded active mounted POSIX Message Queue File System
export-home.mount loaded active mounted /export/home
home.mount loaded active mounted /home
lucien.mount loaded active mounted /lucien
mana-data.mount loaded active mounted /mana/data
run-user-5001.mount loaded active mounted /run/user/5001
sys-kernel-debug.mount loaded active mounted Debug File System
tmp.mount loaded active mounted Temporary Directory
usr-local.mount loaded active mounted /usr/local
usr.mount loaded active mounted /usr
var-lib-nfs-rpc_pipefs.mount loaded active mounted RPC Pipe File System
var.mount loaded active mounted /var
cups.path loaded active running CUPS Scheduler
systemd-ask-password-plymouth.path loaded active waiting Forward Password Requests to Plymouth Directory Watch
systemd-ask-password-wall.path loaded active waiting Forward Password Requests to Wall Directory Watch
session-c1.scope loaded active running Session c1 of user olivier
acpid.service loaded active running ACPI Event Daemon
alsa-state.service loaded active running Manage Sound Card State (restore and store)
atd.service loaded active running Job spooling tools
autofs.service loaded active running Automounts filesystems on demand
avahi-daemon.service loaded active running Avahi mDNS/DNS-SD Stack
bluetooth.service loaded active running Bluetooth service
chronyd.service loaded active running NTP client/server
colord.service loaded active running Manage, Install and Generate Color Profiles
cpupower.service loaded active exited Configure CPU power related settings
crond.service loaded active running Command Scheduler
cups-browsed.service loaded active running Make remote CUPS printers available locally
cups.service loaded active running CUPS Scheduler
dbus.service loaded active running D-Bus System Message Bus
fedora-loadmodules.service loaded active exited Load legacy module configuration
fedora-readonly.service loaded active exited Configure read-only root support
fedora-wait-storage.service loaded active exited Wait for storage scan
ip6tables.service loaded active exited ip6tables Firewall for IPv6
iptables.service loaded active exited iptables Firewall for IPv4
irqbalance.service loaded active running irqbalance daemon
kmod-static-nodes.service loaded active exited Create list of required static device nodes for the current kernel
mandi.service loaded active running Network monitoring daemon (Interactive Firewall and wireless)
mandriva-everytime.service loaded active exited Reconfigure the system on administrator request
mandriva-save-dmesg.service loaded active exited Save boot dmesg content
ModemManager.service loaded active running Modem Manager
msec.service loaded active exited LSB: Enables MSEC security policy on boot
network-up.service loaded active exited LSB: Wait for the hotplugged network to be up
network.service loaded active running LSB: Bring up/down networking
nfs-idmap.service loaded active running NFSv4 ID-name mapping daemon
nfs-lock.service loaded active running NFS file locking service.
● nscd.service loaded failed failed Name Service Cache Daemon
nslcd.service loaded active running Naming services LDAP client daemon
partmon.service loaded active exited LSB: Checks if a partition is close to full up
polkit.service loaded active running Authorization Manager
prefdm.service loaded active running Display Manager
preload.service loaded active running LSB: Adaptive readahead daemon
resolvconf.service loaded active exited LSB: Nameserver information manager
rpcbind.service loaded active running RPC bind service
rtkit-daemon.service loaded active running RealtimeKit Scheduling Policy Service
shorewall.service loaded active exited Shorewall IPv4 firewall
sshd.service loaded active running OpenSSH server daemon
systemd-fsck@dev-disk-by\x2duuid-048c9b12\x2d91c9\x2d43b5\x2db663\x2df5efa3a193c9.service loaded active exited File System Check on /dev/disk/by-uuid/048c9b12-91c9-43b5-b663-f5efa3a193c9
systemd-fsck@dev-disk-by\x2duuid-8b3cee2c\x2dbae2\x2d4e59\x2db210\x2d9fb4c16368f7.service loaded active exited File System Check on /dev/disk/by-uuid/8b3cee2c-bae2-4e59-b210-9fb4c16368f7
systemd-fsck@dev-disk-by\x2duuid-8f5f173b\x2db9c6\x2d45ff\x2d85f8\x2dfdeab49bc328.service loaded active exited File System Check on /dev/disk/by-uuid/8f5f173b-b9c6-45ff-85f8-fdeab49bc328
systemd-fsck@dev-disk-by\x2duuid-dc68a9c3\x2d4f39\x2d460d\x2d89c9\x2d56df20e750b3.service loaded active exited File System Check on /dev/disk/by-uuid/dc68a9c3-4f39-460d-89c9-56df20e750b3
systemd-fsck@dev-disk-by\x2duuid-eafcd3f8\x2d62df\x2d4670\x2d8312\x2d1ffcacefdc1a.service loaded active exited File System Check on /dev/disk/by-uuid/eafcd3f8-62df-4670-8312-1ffcacefdc1a
systemd-journal-flush.service loaded active exited Trigger Flushing of Journal to Persistent Storage
systemd-journald.service loaded active running Journal Service
systemd-logind.service loaded active running Login Service
systemd-modules-load.service loaded active exited Load Kernel Modules
systemd-networkd.service loaded active running Network Service
systemd-random-seed.service loaded active exited Load/Save Random Seed
systemd-remount-fs.service loaded active exited Remount Root and Kernel File Systems
systemd-resolved.service loaded active running Network Name Resolution
systemd-rfkill@rfkill0.service loaded active exited Load/Save RF Kill Switch Status of rfkill0
systemd-rfkill@rfkill1.service loaded active exited Load/Save RF Kill Switch Status of rfkill1
systemd-sysctl.service loaded active exited Apply Kernel Variables
systemd-timesyncd.service loaded active running Network Time Synchronization
systemd-tmpfiles-setup-dev.service loaded active exited Create Static Device Nodes in /dev
systemd-tmpfiles-setup.service loaded active exited Create Volatile Files and Directories
systemd-udev-settle.service loaded active exited udev Wait for Complete Device Initialization
systemd-udev-trigger.service loaded active exited udev Coldplug all Devices
systemd-udevd.service loaded active running udev Kernel Device Manager
systemd-update-utmp.service loaded active exited Update UTMP about System Boot/Shutdown
systemd-user-sessions.service loaded active exited Permit User Sessions
systemd-vconsole-setup.service loaded active exited Setup Virtual Console
udisks2.service loaded active running Disk Manager
upower.service loaded active running Daemon for power management
user@5001.service loaded active running User Manager for UID 5001
-.slice loaded active active Root Slice
system-getty.slice loaded active active system-getty.slice
system-systemd\x2dfsck.slice loaded active active system-systemd\x2dfsck.slice
system-systemd\x2drfkill.slice loaded active active system-systemd\x2drfkill.slice
system.slice loaded active active System Slice
user-5001.slice loaded active active user-5001.slice
user.slice loaded active active User and Session Slice
avahi-daemon.socket loaded active running Avahi mDNS/DNS-SD Stack Activation Socket
cups.socket loaded active running CUPS Scheduler
dbus.socket loaded active running D-Bus System Message Bus Socket
nscd.socket loaded active listening Name Service Cache Daemon Socket
rpcbind.socket loaded active running RPCbind Server Activation Socket
systemd-initctl.socket loaded active listening /dev/initctl Compatibility Named Pipe
systemd-journald-dev-log.socket loaded active running Journal Socket (/dev/log)
systemd-journald.socket loaded active running Journal Socket
systemd-shutdownd.socket loaded active listening Delayed Shutdown Socket
systemd-udevd-control.socket loaded active running udev Control Socket
systemd-udevd-kernel.socket loaded active running udev Kernel Socket
dev-disk-by\x2duuid-b1fada73\x2d7ba6\x2d4692\x2d836b\x2d3b355d1b3fa7.swap loaded active active /dev/disk/by-uuid/b1fada73-7ba6-4692-836b-3b355d1b3fa7
basic.target loaded active active Basic System
bluetooth.target loaded active active Bluetooth
cryptsetup.target loaded active active Encrypted Volumes
getty.target loaded active active Login Prompts
graphical.target loaded active active Graphical Interface
local-fs-pre.target loaded active active Local File Systems (Pre)
local-fs.target loaded active active Local File Systems
multi-user.target loaded active active Multi-User System
network-online.target loaded active active Network is Online
network.target loaded active active Network
nfs.target loaded active active Network File System Client and Server Support
nss-lookup.target loaded active active Host and Network Name Lookups
paths.target loaded active active Paths
remote-fs.target loaded active active Remote File Systems
rpcbind.target loaded active active RPC Port Mapper
slices.target loaded active active Slices
sockets.target loaded active active Sockets
sound.target loaded active active Sound Card
swap.target loaded active active Swap
sysinit.target loaded active active System Initialization
time-sync.target loaded active active System Time Synchronized
timers.target loaded active active Timers
systemd-tmpfiles-clean.timer loaded active waiting Daily Cleanup of Temporary Directories
LOAD = Reflects whether the unit definition was properly loaded.
ACTIVE = The high-level unit activation state, i.e. generalization of SUB.
SUB = The low-level unit activation state, values depend on unit type.
154 loaded units listed. Pass --all to see loaded but inactive units, too.
To show all installed unit files use 'systemctl list-unit-files'.
To stop a unit you will have to type
systemctl stop nom-du-service
and to deactivate it (that is to say that it will no longer launch at the next startup) you will have to type
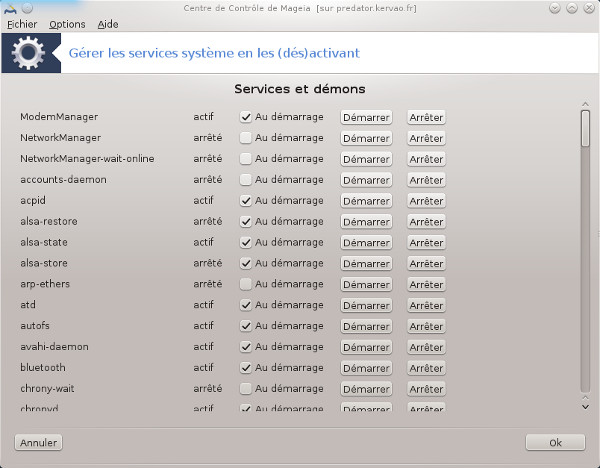
systemctl disable service-namethere are nicer graphical tools to do this like Mageia Control Center
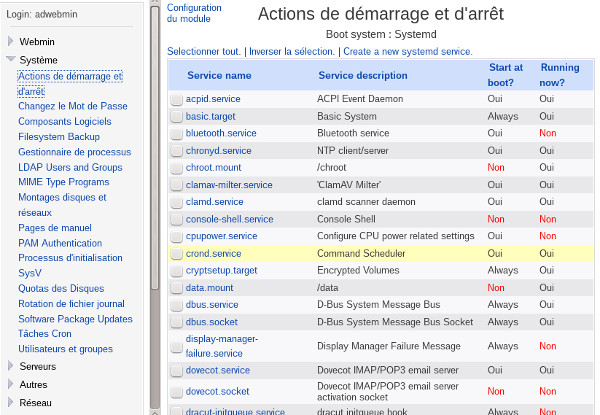
or even via the more universal webmin
Secure /etc/passwd
To activate the shadow password , it is very simple as root, you must type:
pwconv
In the password
field of /etc/passwd (the second one) you should find an x, a file /etc/shadow has been created containing the encrypted
passwords.
Now we will delete as much
as possible all the useless system accounts, if you don't need
them, delete them, because they are so many entry points for
hackers. The following system accounts are necessary:
root, bin, daemon, adm, lp (if you have a printing system), mail (if mail
server), news (if news server), uucp (if you use
UUCP), nobody
These are optional:
games, gopher, halt, sync, shutdown, operator, ftp (if anonymous FTP server), lists, xfs.
Root and Privileged Users
Now for su to be launched only by members of the wheel group, you will have to type:
chmod 4750 /bin/su
Do the same for the other commands.
NOTES : - Remember that a user can very well belong to two groups- Don't forget sudo to give privileged rights to certain users.
As for root, you must take
some precautions:
- you must not add the . (current
directory) in the root PATH, because if by misfortune someone
creates a script with executable rights in /tmp called rm containing:
#!/bin/bash
rm -Rf /
If root has the misfortune to type rm while in /tmp , this is the script that can be called (following the order of the paths in the PATH) and poof! no more system.
Secure Files and File Systems
1) SUID and GUID
Avoid using SUID and SGID, they carry some security risks, they allow anyone to launch a program with the rights of the program owner. SUID files are one of the main targets of hackers, so avoid them, prefer sudo .To find files with SUID or SGID, type as root:
find / -type f \( -perm 04000 -o -perm 02000 \)
2) .rhosts and hosts.equiv files
We saw above that we should avoid having .rhosts or hosts.equiv files , so we will block these two files so that no one can recreate them. To block the files, simply type the commands:touch /.rhosts
/etc/hosts.equiv
chmod 0 /.rhosts
/etc/hosts.equiv
To find .rhosts in users' home directories, type:
find /home -name .rhosts -print
3) Umask
We can define the default creation rights of a file or directory with the umask command , we will make sure to avoid creating directories with the 777 rights.To define the umask for all users of the system, you must edit the /etc/profile file and modify the line concerning umask, you can set 022, 027 or even 077 which is the most restrictive mask (see my unix course to see how umask works ).
Install a firewall with shorewall
Shorewall configuration level , this gives this, all the files are under /etc/shorewall , that's it for the zones file
# Shorewall version 4 – Zones File
#
# For information about this file, type “man shorewall-zones”
#
# The manpage is also online at
# http://www.shorewall.net/manpages/shorewall-zones.html
#
#############################################################################
#ZONE TYPE OPTIONS IN OUT
# OPTIONS OPTIONS
fw firewall
lan ipv4
the fw zone corresponds to the server that acts as a firewall, the lan zone corresponds indifferently to the internet and the local network. Here is now the interfaces file
# Shorewall version 4 – Interfaces File
#
# For information about entries in this file, type “man shorewall-interfaces”
#
# The manpage is also online at
# http://www.shorewall.net/manpages/shorewall-interfaces.html
#
#############################################################################
##############################################################################
#INTERFACE OPTIONS ZONE OPTIONS
lan eno2 –
my network card used is defined by eno2 , my eno1 card is not used, the ifconfig -a command allows you to know the name of its network interfaces. the hosts file is empty (or almost)
# Shorewall version 4 – Hosts file
#
# For information about entries in this file, type “man shorewall-hosts”
#
# The manpage is also online at
# http://www.shorewall.net/manpages/shorewall-hosts.html
#
############################################################################
#HOST ZONE OPTIONS
the policy file defines the default rules
# Shorewall version 4 – Policy File
#
# For information about entries in this file, type “man shorewall-policy”
#
# The manpage is also online at
# http://www.shorewall.net/manpages/shorewall-policy.html
#
#############################################################################
#SOURCE DEST POLICY LOG LIMIT: CONNLIMIT:
fw lan ACCEPT
all all REJECT info
basically all frames from the server to the internet are accepted and all others are rejected, so you need to define some exceptions with the rules file here
# Shorewall version 4 – Rules File
#
# For information on the settings in this file, type “man shorewall-rules”
#
# The manpage is also online at
# http://www.shorewall.net/manpages/shorewall-rules.html
#
############################################################################################### ###############################################################################################
#ACTION SOURCE DEST PROTO DEST SOURCE ORIGINAL RATE USER/ MARK CONNLIMIT TIME HEADERS SWITCH HELPER
# PORT(S) PORT(S) DEST LIMIT GROUP
ACCEPT fw lan icmp
ACCEPT lan:192.168.1.0/24 fw tcp 22,25,80,111,389,995,2049,3306,10000
ACCEPT lan:192.168.1.0/24 fw udp 111.2049
ACCEPT lan:192.168.1.0/24 fw icmp
DNS(ACCEPT) fw lan
Machines on the local network with address 192.168.1.X are allowed to access the server on port 22 ( OpenSSH ), 25 ( SMTP ), 80 ( Apache/httpd ), 111 ( portmapper ), 389 ( OpenLDAP ), 995 ( POP3s ), 2049 ( NFS ), 3306 ( MySQL ) and 10000 ( Webmin ). DNS queries from the server to the internet are also allowed and pings are also allowed .
Now the server can still be reached via client stations and these must also be protected. I have limited the traffic to and from the internet to the strict minimum, always with shorewall . Example of configuration of a client connected via an RJ45 interface that can be pinged, zones file
# Shorewall version 4 – Zones File
#
# For information about this file, type “man shorewall-zones”
#
# The manpage is also online at
# http://www.shorewall.net/manpages/shorewall-zones.html
#
#############################################################################
#ZONE TYPE OPTIONS IN OUT
# OPTIONS OPTIONS
net ipv4
fw firewall
interfaces file
# Shorewall version 4 – Interfaces File
#
# For information about entries in this file, type “man shorewall-interfaces”
#
# The manpage is also online at
# http://www.shorewall.net/manpages/shorewall-interfaces.html
#
#############################################################################
##############################################################################
#ZONE INTERFACE OPTIONS
net eno1 detect
empty hosts file , policy file
# Shorewall version 4 – Policy File
#
# For information about entries in this file, type “man shorewall-policy”
#
# The manpage is also online at
# http://www.shorewall.net/manpages/shorewall-policy.html
#
#############################################################################
#SOURCE DEST POLICY LOG LIMIT: CONNLIMIT:
fw net ACCEPT
net all DROP info
all all REJECT info
and rules file
# Shorewall version 4 – Rules File
#
# For information on the settings in this file, type “man shorewall-rules”
#
# The manpage is also online at
# http://www.shorewall.net/manpages/shorewall-rules.html
#
################################################################################################ ################################################################################################
#ACTION SOURCE DEST PROTO DEST SOURCE ORIGINAL RATE USER/ MARK CONNLIMIT TIME HEADERS SWITCH HELPER
# PORT(S) PORT(S) DEST LIMIT GROUP
ACCEPT net fw icmp 8 –
Filter with villain IP lists
The purpose of this chapter is to explain to you how to set up lists of IP addresses recognized as being a potential threat. It turns out that certain entities are responsible for collecting these lists and making them available to the community. All that remains is to have them taken into account by the shorewall firewall which will block the IP addresses from the outset.
The source of this chapter is mainly the mageia wiki in English at https://wiki.mageia.org/en/Firewall or you can also consult this entry from the mageia forum.
This filtering is based on shorewall but also on the ipset tool . IPset allows you to store lists of IP addresses, but also networks, port numbers, MAC addresses or even combinations of all of these. Intrinsically IPtables on which shorewall is based could do the same thing, but IPset is optimized so that indexing and searching in the list is infinitely faster.
This page simply explains to you how IPset works.
IPset is linked to the Linux kernel, it will be necessary to install the following packages on a Mageiaurpmi xtables-addons xtables-geoip xtables-addons-kernel-desktop-latest
To see if IPset is well integrated, you will have to typeshorewall show capabilities | grep Ipset
This is the result
Ipset Match Counters
(IPSET_MATCH_COUNTERS): Available
Ipset Match
(IPSET_MATCH): Available
Ipset Match Nomatch
(IPSET_MATCH_NOMATCH): Available
For the lists of threatening IP addresses, we will use those of the abuseipdb and spamhaus sites . Now we will have to create an account for the first one and retrieve a key that we will use to download the list.
We will now create the following script /usr/bin/shorewall-vilains which will contain#!/bin/bash
# Script origin
#
https://wiki.mageia.org/en/Firewall
###########################
# Defining multiple
variables
# for IP address lists
SPAMHAUS_DROP="/usr/local/var/drop.txt"
SPAMHAUS_eDROP="/usr/local/var/edrop.txt"
ABUSE_DROP="/usr/local/var/abuseip.txt"
SPAMURL="https://www.spamhaus.org/drop/drop.txt"
eSPAMURL="https://www.spamhaus.org/drop/edrop.txt"
DROP_ADD_TO_FW="/usr/local/var/DROP2.txt"
eDROP_ADD_TO_FW="/usr/local/var/eDROP2.txt"
ABUSE_ADD_TO_FW="/usr/local/var/abuseipv4.txt"
SAVE_SPAM="/etc/shorewall/spamhaus"
SAVE_SPAME="/etc/shorewall/espamhaus"
SAVE_ABUSE="/etc/shorewall/abuseipdb"
# Name of lists for the
ABUSE
firewall="abusedrop";
SPAM="spamhausdrop";
SPAME="spamhausedrop";
#
echo ">>"
echo "Start: $(date)"
echo ">"
#
# Purge previous IP
#
echo "Creating ipset DROP
rules"
/usr/sbin/ipset -exist
create $ABUSE hash:net counters
/usr/sbin/ipset -exist
create $SPAM hash:net counters
/usr/sbin/ipset -exist
create $SPAME hash:net counters
echo "Purge old ipset DROP
rules"
/usr/sbin/ipset flush
$ABUSE
/usr/sbin/ipset flush
$SPAM
/usr/sbin/ipset flush
$SPAME
#
# ABUSEIPDB.com
echo "Download ABUSEIP
list and extract IPs"
curl -G
https://api.abuseipdb.com/api/v2/blacklist -d
confidenceMinimum=90 -H "Key:
we-indicate-here-the-key-retrieved-from-abuseipdb" -H
"Accept: text/plain" > $ABUSE_DROP
#clears IPv6
sed '/:/d' $ABUSE_DROP
> $ABUSE_ADD_TO_FW
echo "Updating ipset with
ABUSE list"
while read IP; do
/usr/sbin/ipset -exist add $ABUSE $IP
done <
"$ABUSE_ADD_TO_FW"
echo "IPSET save ABUSE
list"
/usr/sbin/ipset save
$ABUSE > $SAVE_ABUSE
# "The Spamhaus Project" -
https://www.spamhaus.org
#
echo ">"
echo "Downloading SPAMHAUS
DROP list and extracting IPs"
wget -q -O - "$SPAMURL"
> $SPAMHAUS_DROP
grep -v '^;'
$SPAMHAUS_DROP | cut -d ' ' -f 1 > $DROP_ADD_TO_FW
echo "Updating ipset with
SPAMHAUS DROP list"
while read IP; do
/usr/sbin/ipset -exist add $SPAM $IP
done <
"$DROP_ADD_TO_FW"
echo "Save ipset SPAMHAUS
list"
/usr/sbin/ipset save $SPAM
> $SAVE_SPAM
#
# "The Spamhaus Project" -
https://www.spamhaus.org
#
echo ">"
echo "Download SPAMHAUS
eDROP list and extract IPs"
wget -q -O - "$eSPAMURL"
> $SPAMHAUS_eDROP
grep -v '^;'
$SPAMHAUS_eDROP | cut -d ' ' -f 1 > $eDROP_ADD_TO_FW
echo "Updating ipset with
SPAMHAUS eDROP list"
while read IP; do
/usr/sbin/ipset -exist add $SPAME $IP
done <
"$eDROP_ADD_TO_FW"
echo "Save ipset with
eSPAMHAUS list"
/usr/sbin/ipset save
$SPAME > $SAVE_SPAME
#
# Activation of new lists
# by restarting the
firewall
#
echo ">"
echo "Restarting the
firewall"
echo "--------------- "
/usr/sbin/shorewall
restart
#
# Checks
#
echo " "
/usr/bin/systemctl status
--no-pager shorewall
echo " "
/usr/sbin/shorewall show
bl
echo " "
echo "Number of
spamhausDrop list lines"
/usr/sbin/ipset list
"$SPAM" | wc -l
echo "Number of
spamhauseDrop list lines"
/usr/sbin/ipset list
"$SPAME" | wc -l
echo "Number of abusedrop
list lines"
/usr/sbin/ipset list
"$ABUSE" | wc -l
echo ">"
echo End: $(date)
echo ">>"
he is given execution rights
chmod 755 /usr/bin/shorewall-villains
This is what it looks like when you launch it
>>
Start: Sun Sep 5 08:10:50
CEST 2021
>
Creation of ipset DROP
rules
We purge the old ipset
DROP rules
Download ABUSEIP list and
extract IPs
% Total % Received
% Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 139k 0 139k 0 0 185k
0 --:--:-- --:--:-- --:--:-- 185k
Update ipset with ABUSE
list
Update firewall with ABUSE
rules
Backup ipset of ABUSE list
>
Download SPAMHAUS DROP
list and extract IPs
Update ipset with SPAMHAUS
DROP list
Backup ipset of SPAMHAUS
list
>
Download SPAMHAUS eDROP
list and extract IPs
Update ipset with SPAMHAUS
eDROP list
Backup ipset with
eSPAMHAUS list
>
Restarting the firewall
---------------
Compiling using Shorewall
5.2.3.3...
Processing
/etc/shorewall/params ...
Processing
/etc/shorewall/shorewall.conf...
Loading Modules...
Compiling
/etc/shorewall/zones...
Compiling
/etc/shorewall/interfaces...
Determining Hosts in
Zones...
Locating Action Files...
Compiling
/etc/shorewall/policy...
Running
/etc/shorewall/initdone...
Compiling TCP Flags
filtering...
Compiling Kernel Route
Filtering...
Compiling Martian
Logging...
Compiling MAC Filtration
-- Phase 1...
Compiling
/etc/shorewall/blrules...
Compiling
/etc/shorewall/rules...
Compiling
/etc/shorewall/conntrack...
Compiling
/etc/shorewall/tunnels...
Compiling MAC Filtration
-- Phase 2...
Applying Policies...
Generating Rule Matrix...
Creating iptables-restore
input...
Shorewall configuration
compiled to /var/lib/shorewall/.restart
Stopping Shorewall....
Processing
/etc/shorewall/stop ...
Processing
/etc/shorewall/tcclear ...
Preparing iptables-restore
input...
Running
/sbin/iptables-restore --wait 60...
Processing
/etc/shorewall/stopped ...
done.
Starting Shorewall....
Initializing...
Processing
/etc/shorewall/init ...
Processing
/etc/shorewall/tcclear ...
Setting up Route
Filtering...
Setting up Martian
Logging...
Setting up Proxy ARP...
Preparing iptables-restore
input...
Running
/sbin/iptables-restore --wait 60...
Processing
/etc/shorewall/start ...
Processing
/etc/shorewall/started ...
done.
● shorewall.service -
Shorewall IPv4 firewall
Loaded:
loaded (/usr/lib/systemd/system/shorewall.service; disabled;
vendor preset: enabled)
Active:
active (exited) since Sat 2021-09-04 20:00:07 CEST; 12h ago
Process: 5834
ExecStart=/sbin/shorewall $OPTIONS start $STARTOPTIONS
(code=exited, status=0/SUCCESS)
Main PID: 5834
(code=exited, status=0/SUCCESS)
Sep 04 20:00:07
mana.kervao.fr shorewall[5834]: Setting up Martian
Logging...
Sep 04 20:00:07
mana.kervao.fr shorewall[5834]: Setting up Proxy ARP...
Sep 04 20:00:07
mana.kervao.fr shorewall[5834]: Preparing iptables-restore
input...
Sep 04 20:00:07
mana.kervao.fr shorewall[5834]: Running
/sbin/iptables-restore --wait 60...
sept. 04 20:00:07
mana.kervao.fr shorewall[5834]: Processing
/etc/shorewall/start ...
Sep 04 20:00:07
mana.kervao.fr shorewall[5834]: ipset v7.10: Set cannot be
created: set with the same name already exists
Sep 04 20:00:07
mana.kervao.fr shorewall[5834]: ipset v7.10: Set cannot be
created: set with the same name already exists
Sep 04 20:00:07
mana.kervao.fr shorewall[5834]: Processing
/etc/shorewall/started ...
Sep 04 20:00:07
mana.kervao.fr shorewall[5834]: done.
Sep 04 20:00:07
mana.kervao.fr systemd[1]: Started Shorewall IPv4 firewall.
Shorewall 5.2.3.3
blacklist chains at mana.kervao.fr - Sun Sep 5 08:11:15 CEST
2021
Chain dynamic (4
references)
pkts bytes target
prot opt in out source
destination
Chain lan-fw~ (1
references)
pkts bytes target
prot opt in out source
destination
0 0
~log0 all -- * * 0.0.0.0/0 0.0.0.0/0 [goto] match-set
abusedrop src
0 0
~log2 all -- * * 0.0.0.0/0 0.0.0.0/0 [goto] match-set
spamhausdrop src
0 0
~log4 all -- * * 0.0.0.0/0 0.0.0.0/0 [goto] match-set
spamhausedrop src
Chain lan-vpn~ (1
references)
pkts bytes target
prot opt in out source
destination
0 0
~log1 all -- * * 0.0.0.0/0 0.0.0.0/0 [goto] match-set
abusedrop src
0 0
~log3 all -- * * 0.0.0.0/0 0.0.0.0/0 [goto] match-set
spamhausdrop src
0 0
~log5 all -- * * 0.0.0.0/0 0.0.0.0/0 [goto] match-set
spamhausedrop src
Number of lines in
spamhausDrop list
1054
Number of lines in
spamhauseDrop list
78
Number of lines in
abusedrop list
10007
>
End: Sun Sep 5 08:11:15
CEST 2021
>>
Now to have the lists updated daily, you just need to create a link under /etc/cron.daily
ln -s /usr/bin/shorewall-villains /etc/cron.daily/
The "control" lines of the script allow you to check that everything is working properly, we find in particular the command
shorewall show bl
who gives
Shorewall 5.2.3.3 blacklist
chains at mana.kervao.fr - Sat Sep 4 20:04:25 CEST 2021
Chain dynamic (4
references)
pkts bytes target
prot opt in out source
destination
Chain lan-fw~ (1
references)
pkts bytes target
prot opt in out source
destination
0 0
~log0 all -- * * 0.0.0.0/0 0.0.0.0/0 [goto] match-set
abusedrop src
0 0
~log2 all -- * * 0.0.0.0/0 0.0.0.0/0 [goto] match-set
spamhausdrop src
0 0
~log4 all -- * * 0.0.0.0/0 0.0.0.0/0 [goto] match-set
spamhausedrop src
Chain lan-vpn~ (1
references)
pkts bytes target
prot opt in out source
destination
0 0
~log1 all -- * * 0.0.0.0/0 0.0.0.0/0 [goto] match-set
abusedrop src
0 0
~log3 all -- * * 0.0.0.0/0 0.0.0.0/0 [goto] match-set
spamhausdrop src
0 0
~log5 all -- * * 0.0.0.0/0 0.0.0.0/0 [goto] match-set
spamhausedrop src
and the ipset list command lists the banned IP addresses, this gives
Name: abusedrop
Type: hash:net
Revision: 6
Header: family inet
hashsize 4096 maxelem 65536
Size in memory: 268360
References: 2
Number of entries: 9998
Members:
42.193.0.6
192.241.221.234
98.214.176.181
43.128.89.158
167.99.132.148
(...)
Name: spamhausdrop
Type: hash:net
Revision: 6
Header: family inet
hashsize 1024 maxelem 65536 counters
Size in memory: 86848
References: 2
Number of entries: 1046
Members:
102.212.224.0/19 packets 0
bytes 0
204.87.136.0/24 packets 0
bytes 0
206.197.29.0/24 packets 0
bytes 0
168.151.0.0/22 packets 0
bytes 0
199.26.207.0/24 packets 0
bytes 0
(...)
Name: spamhausedrop
Type: hash:net
Revision: 6
Header: family inet
hashsize 1024 maxelem 65536 counters
Size in memory: 9280
References: 2
Number of entries: 70
Members:
43.57.0.0/16 packets 0
bytes 0
120.64.0.0/16 packets 0
bytes 0
46.148.120.0/24 packets 0
bytes 0
120.67.0.0/16 packets 0
bytes 0
204.141.204.0/24 packets 0
bytes 0
91.208.245.0/24 packets 0
bytes 0
45.143.136.0/22 packets
0 bytes 0
91.243.93.0/24 packets 0
bytes 0
(...)
Name: ifw_wlType: hash:ip
Revision: 4
Header: family inet hashsize 1024 maxelem 65536
Size in memory: 200
References: 1
Number of entries: 0
Members:
Name: ifw_bl
Type: hash:ip
Revision: 4
Header: family inet hashsize 1024 maxelem 65536 timeout 3600
Size in memory: 200
References: 1
Number of entries: 0
Members:
To ensure that these lists are maintained upon reboot, you will need to modify the /etc/shorewall/init file by adding
# Restore
Abuseipdb and Spamhauss lists
if [ -f
/etc/shorewall/abuseipdb ]; then
ipset destroy
abusedrop
ipset -file
/etc/shorewall/abuseipdb restore
fi
if [ -f
/etc/shorewall/spamhaus ]; then
ipset destroy
spamhausdrop
ipset -file
/etc/shorewall/spamhaus restore
fi
if [ -f
/etc/shorewall/espamhaus ]; then
ipset destroy
spamhausedrop
ipset -file
/etc/shorewall/espamhaus restore
fi
You can
manually add an IP address by typing (you will need to specify
the name of a list)
ipset add spamhaus ip-address
and remove an
address
ipset from
spamhaus ip address
Check and audit your system under Mageia
It is also useful to take a snapshot of your system and do a regular check to see if nothing has changed, MSEC does this very well under Mageia, for the record MSEC means Mandriva Security Settings, it is accessed via the Mageia control center (CCM). From this page you have access to the reports, these can also be sent to an email.
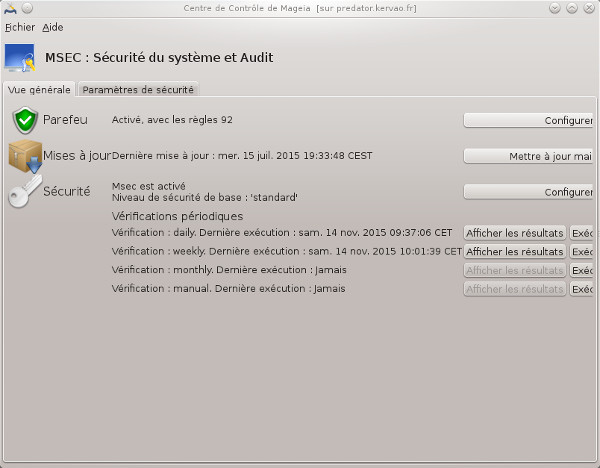
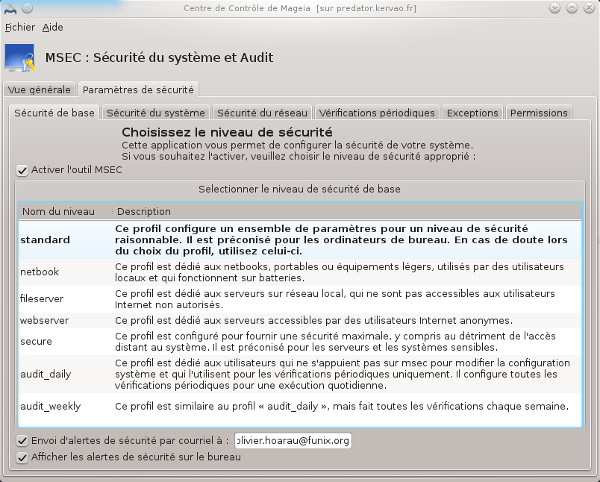
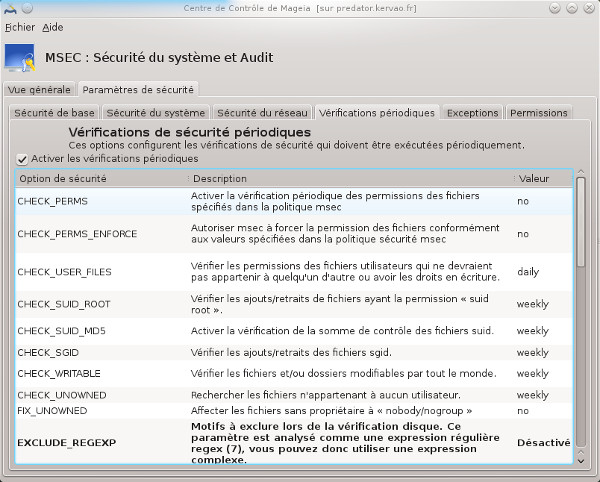
tab you have other settings but this time they concern the network. In the Periodic Checks tab you have the frequency of checking by theme.
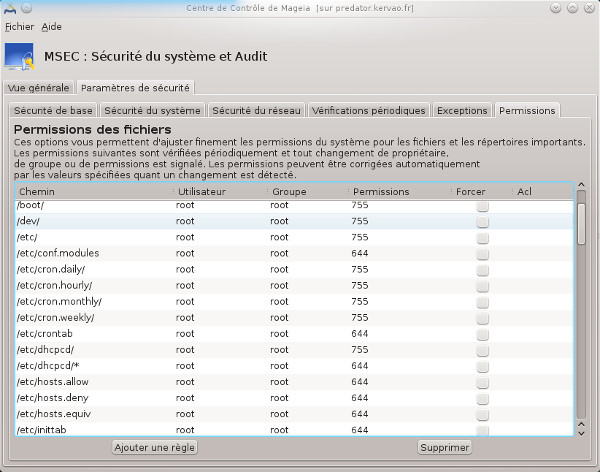
In the Permissions tab you define the permissions of important files and directories, in case of change you are warned and the system can force a return to the initial values.
| [ Back to FUNIX home page ] | [ Back to top of page ] |
 Welcome
Welcome Linux
Linux Unix
Unix Download
Download