Setting up a private VPN network with OpenVPN
Last modified October 10, 2021This site has been automatically translated with Google Translate from this original page written in french, there may be some translation errors
Presentation
This page aims to present the configuration of a private VPN network with OpenVPN. A VPN (Virtual Private Network) allows remote access to a local network transparently as if you were connected directly to the local network. To do this, the VPN will establish a secure and encrypted communication tunnel among the internet traffic to allow exchanges. The interest of a VPN is multiple, it allows (non-exhaustive list):
- to be able to remotely access the resources of a local network as mentioned previously;
- to pass all internet traffic to the local network, which allows (among other things):
- to set up internet filtering (often in the case of professional use);
- to be able to freely access the internet via the VPN (in case you are in a country that restricts internet access).
In my case, it is about being able to access a private local network from a remote PC connected to the internet via wifi via a mobile with 4G connection. This allows me to be able to access the resources of my local network wherever I am. Be careful, most of the configurations presented on the internet and in particular the pages listed below present a configuration where all the flow to the client's internet goes through the VPN network, this is surely interesting for certain needs but in my case it is a perfectly useless intermediary that slows down the client's internet access. However, if you are more interested in internet access via VPN, I advise you to read the pages indicated below in the sources.
In summary, the configuration presented on this page allows access to the resources of a local network via VPN but does not allow the client to access the Internet via the VPN (he can nevertheless access it with his own direct connection).
Installation and configuration was done on Mageia, but it should adapt quite easily to all distributions.
In the following operations:
- my server is called mana has a local address 192.168.1.11 with a local network that uses the 192.168.1.X network. The network interface is eno2.
- the client is called tetiaroa and is connected via wifi to a 4G mobile which assigns it the address 192.168.43.70 on the 192.168.43.X network (information visible by typing ifconfig -a )
The complete network topology is as follows
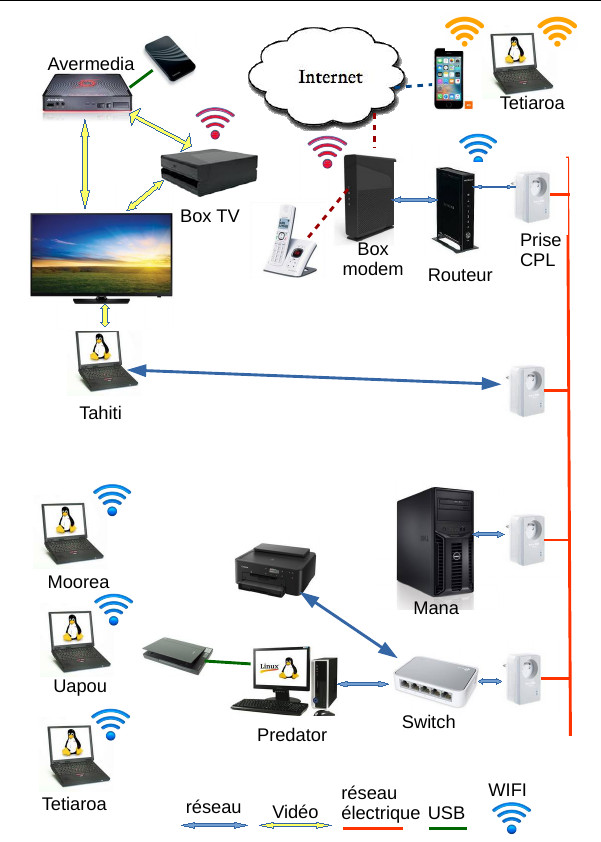
I create a VPN link between the tetiaroa station clearly visible at the top right with the mana server via the 4G mobile which shares its connection, internet, the box and a router.
The sources I used to write this page are:
- https://open-freax.fr/monter-vpn-openvpn/
- https://www.mageialinux-online.org/forum/topic-21409-2+se-connecter-a-un-serveur-vpn.php
- https://www.mageialinux-online.org/wiki/configurer-son-serveur-et-ses-clients-vpn-sous-mageia
- https://openvpn.net/community-resources/how-to/
- https://doc.ubuntu-fr.org/openvpn
- https://documentation.online.net/fr/dedicated-server/tutorials/service/configure-vpn
Server Installation and Configuration
Facility
For the installation, for once I was content to use the package provided with my distribution which we will install as
urpmi openvpn
you just need to adapt it to the package manager of your distribution.
Creating encryption keys
For the principle of the certification authority, private and public keys to secure exchanges, I refer you to this page which gives the main principles.
Now we will set up the files to launch the configuration, we install the configuration files provided by the package by copying them under /etc/openvpn which was normally created when the package was installed
cp -r /usr/share/openvpn/easy-rsa /etc/openvpn
We edit the file /etc/openvpn/easy-rsa/vars and modify it as follows
# easy-rsa parameter settings
# NOTE: If you installed from an RPM,
# don't edit this file in place in
# /usr/share/openvpn/easy-rsa --
# instead, you should copy the whole
# easy-rsa directory to another location
# (such as /etc/openvpn) so that your
# edits will not be wiped out by a future
# OpenVPN package upgrade.
# This variable should point to
# the top level of the easy-rsa
# tree.
# on indique le chemin du répertoire easy-rsa
export EASY_RSA="/etc/openvpn/easy-rsa"
#
# This variable should point to
# the requested executables
#
export OPENSSL="openssl"
export PKCS11TOOL="pkcs11-tool"
export GREP="grep"
# This variable should point to
# the openssl.cnf file included
# with easy-rsa.
export KEY_CONFIG=`$EASY_RSA/whichopensslcnf $EASY_RSA`
# Edit this variable to point to
# your soon-to-be-created key
# directory.
#
# WARNING: clean-all will do
# a rm -rf on this directory
# so make sure you define
# it correctly!
export KEY_DIR="$EASY_RSA/keys"
# Issue rm -rf warning
echo NOTE: If you run ./clean-all, I will be doing a rm -rf on
$KEY_DIR
# PKCS11 fixes
export PKCS11_MODULE_PATH="dummy"
export PKCS11_PIN="dummy"
# Increase this to 2048 if you
# are paranoid. This will slow
# down TLS negotiation performance
# as well as the one-time DH parms
# generation process.
export KEY_SIZE=2048
# In how many days should the root CA key expire?
export CA_EXPIRE=3650
# In how many days should certificates expire?
export KEY_EXPIRE=3650
# These are the default values for fields
# which will be placed in the certificate.
# Don't leave any of these fields blank.
export KEY_COUNTRY="FR"
export KEY_PROVINCE="Bretagne"
export KEY_CITY="BreizhCity"
export KEY_ORG="Funix"
export KEY_EMAIL="olivier.hoarau@funix.org"
export KEY_EMAIL=olivier.hoarau@funix.org
export KEY_CN=mana
export KEY_NAME=mana
export KEY_OU=funix
export PKCS11_MODULE_PATH=""
export PKCS11_PIN=1234
In practice I just indicated the path of easy-rsa, increased the key size to 2048 (instead of 1024) and entered all the information concerning the country, the region (province), the city (city), the organization, the email, the unique identification (common name), the name of the server and the organization (organizational unit). It would seem for a private network that it does not have a big impact if we put a little crazy values.
Note that everything related to PKCS#11 concerns physical equipment such as dongle, PCMCIA card, microSD or USB key with integrated encryption key "cryptographic tokens" which allows you to connect and which gives additional security, because without this physical key, no connection. For my part I don't have one, so I forget.
Now we check the version of openssl (which must be installed) by typing
openssl version
at my place it gives
OpenSSL 1.1.0l Sep 10, 2019
so in the /etc/openvpn/easy-rsa directory I created the following link
ln -s openssl-1.0.0.cnf openssl.cnf
The new configuration is created from the information provided in vars by typing
source vars
here is the result
NOTE: If you run ./clean-all, I will be doing a rm -rf on /etc/openvpn/easy-rsa/keys
For security reasons, we clean up to start from a blank configuration and delete any old keys found under /etc/openvpn/easy-rsa/keys by typing
./clean-all
We now generate the certificates of the certification authority with the command
./build-ca
here is the result
Generating a
RSA private key
...................................+++++
...............+++++
writing new private key to
'ca.key'
-----
You are about to be asked
to enter information that will be incorporated
into your certificate
request.
What you are about to
enter is what is called a Distinguished Name or a DN.
There are quite a few
fields but you can leave some blank
For some fields there will
be a default value,
If you enter '.', the
field will be left blank.
-----
Country Name (2 letter
code) [FR]:FR
State or Province Name
(full name) [Bretagne]:Bretagne
Locality Name (eg, city)
[BreizhCity]:
Organization Name (eg,
company) [Funix]:
Organizational Unit Name
(eg, section) [funix]:
Common Name (eg, your name
or your server's hostname) [mana]:
Name [mana]:mana
Email Address
[olivier.hoarau@funix.org]:
I hit Enter each time, because it takes the information entered in the vars file. As a reminder, the certification authority or trusted third party is used to authenticate public keys, in practice we create a personal certification authority that will not be recognized on the internet but it does not harm the operation, see here for more details.
Now we will create the server private key and certify it with the personal certification authority by typing
./build-key-server mana
here is the result
Generating a RSA private key
....................+++++
.............................................................+++++
writing new private key to 'mana.key'
-----
You are about to be asked to enter information that will be
incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished
Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [FR]:
State or Province Name (full name) [Bretagne]:
Locality Name (eg, city) [BreizhCity]:
Organization Name (eg, company) [Funix]:
Organizational Unit Name (eg, section) [funix]:
Common Name (eg, your name or your server's hostname) [mana]:
Name [mana]:
Email Address [olivier.hoarau@funix.org]:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Using configuration from /etc/openvpn/easy-rsa/openssl.cnf
Can't open /etc/openvpn/easy-rsa/keys/index.txt.attr for
reading, No such file or directory
139865288554304:error:02001002:system library:fopen:No such file
or
directory:crypto/bio/bss_file.c:74:fopen('/etc/openvpn/easy-rsa/keys/index.txt.attr','r')
139865288554304:error:2006D080:BIO routines:BIO_new_file:no such
file:crypto/bio/bss_file.c:81:
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName
:PRINTABLE:'FR'
stateOrProvinceName :PRINTABLE:'Bretagne'
localityName
:PRINTABLE:'BreizhCity'
organizationName
:PRINTABLE:'Funix'
organizationalUnitName:PRINTABLE:'funix'
commonName
:PRINTABLE:'mana'
name
:PRINTABLE:'mana'
emailAddress
:IA5STRING:'olivier.hoarau@funix.org'
Certificate is to be certified until Jul 20 12:29:52 2031 GMT
(3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
Note that I left a blank field at the challenge password level. The interest of the latter is a little obscure, you will find an explanation here .
We now generate the private key for the openvpn client station which will be a thinkpad named tetiaroa and we certify the key
./build-key-pass tetiaroa
This is the result
Generating a RSA private key
..................................+++++
...........................+++++
writing new private key to 'tetiaroa.key'
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----
You are about to be asked to enter information that will be
incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished
Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [FR]:
State or Province Name (full name) [Bretagne]:
Locality Name (eg, city) [BreizhCity]:
Organization Name (eg, company) [Funix]:
Organizational Unit Name (eg, section) [funix]:
Common Name (eg, your name or your server's hostname)
[tetiaroa]:
Name [mana]:tetiaroa
Email Address [olivier.hoarau@funix.org]:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Using configuration from /etc/openvpn/easy-rsa/openssl.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName
:PRINTABLE:'FR'
stateOrProvinceName :PRINTABLE:'Bretagne'
localityName
:PRINTABLE:'BreizhCity'
organizationName
:PRINTABLE:'Funix'
organizationalUnitName:PRINTABLE:'funix'
commonName
:PRINTABLE:'tetiaroa'
name
:PRINTABLE:'tetiaroa'
emailAddress
:IA5STRING:'olivier.hoarau@funix.org'
Certificate is to be certified until Jul 20 12:33:48 2031 GMT
(3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
You must enter a password at the "PEM pass phrase" level, it will be useful when you launch the client connection. However, there too, it is useless to enter the challenge password. We will now add additional security that we may consider superfluous by encrypting the client's private key with the 3DES algorithm by typing
openssl rsa -in tetiaroa.key -des3 -out tetiaroa.3des.key
here is the result
Enter pass
phrase for tetiaroa.key:
writing RSA key
Enter PEM pass phrase:
Verifying - Enter PEM pass
phrase:
I entered the same password that was used when the client's private key was initially generated.
We will now set up a key exchange called Diffie-Hellman , this is an additional security that will allow the server and the client "to agree on a number (which they can use as a key to encrypt the following conversation) without a third agent (...) being able to discover the number, even after having listened to all their exchanges" (extract from the Wikipedia page on Diffie-Hellman )
To generate the Diffie Hellman parameters for the server we will type
./build-dh
here is the result
Generating DH parameters, 2048
bit long safe prime, generator 2
This is going to take a long time
........+...................................................................................................................................................................................................+............................
....................................................................+...........................................................+.........................................................................................................
....................................+.........................................................................................................................................+..................+.......................................
(...)
....................................................................................................................................................................................................................................+...............................................................................................................+.+..............................................................................................+...................................................
.................................+.........................................................++*++*++*++*
it's longer than the previous commands, I shortened the output above.
Now we will create an HMAC (Hash-Based Message Authentication Code) key which adds additional security against DoS (Denial of Service) attacks, the client will have to present the HMAC key known to the server to start the dialogue, otherwise it is rejected outright without going any further.
When someone tries to connect without being known, it could generate this kind of message on the server
Jul 24 11:12:02 mana.kervao.fr openvpn[26146]: TLS Error: cannot locate HMAC in incoming packet from [AF_INET]185.200.118.41:33825
To create this HMAC key we type
openvpn --genkey --secret keys/ta.key
Now we will find all the keys in the directory /etc/openvpn/easy-rsa/keys . Here is the detail of each of the keys
| File | Used by | Content | Private |
| ca.crt | server and clients | CA Certificate Authority Certificate | No |
| ca.key | Key signing machine only | CA Certificate Authority Private Key | Yes |
| dh2048.pem | server only | Diffie Hellman Parameters | No |
| mana.crt | server only | Certificate of Mana | No |
| mana.key | server only | Mana Private Key | Yes |
| tetiaroa.crt | customer only | Tetiaroa Certificate | No |
| tetiaroa.key | customer only | tetiaroa's private key | Yes |
| your.key | server and clients | HMAC Private Key | Yes |
Configuration
We will copy a default configuration file installed during the installation of the package by typing
cp /usr/share/openvpn/sample-config-files/server.conf /etc/openvpn
Here is its commented content
################################################ Sample OpenVPN 2.0 config file for #
# multi-client server. #
# #
# This file is for the server side #
# of a many-clients <-> one-server #
# OpenVPN configuration. #
# #
# OpenVPN also supports #
# single-machine <-> single-machine #
# configurations (See the Examples page #
# on the web site for more info). #
# #
# This config should work on Windows #
# or Linux/BSD systems. Remember on #
# Windows to quote pathnames and use #
# double backslashes, eg: #
# "C:\\Program Files\\OpenVPN\\config\\foo.key" #
# #
# Comments are preceded with '#' or ';' #
###############################################
# Which local IP address should OpenVPN
# listen on? (optional)
# local address of the
local server 192.168.1.11
# Which TCP/UDP port should OpenVPN listen on?
# If you want to run multiple OpenVPN instances
# on the same machine, use a different port
# number for each one. You will need to
# open up this port on your firewall.
port 1194
# TCP or UDP server?
;proto tcp
proto udp
# "dev tun" will create a routed IP tunnel,
# "dev tap" will create an ethernet tunnel.
# Use "dev tap0" if you are ethernet bridging
# and have precreated a tap0 virtual interface
# and bridged it with your ethernet interface.
# If you want to control access policies
# over the VPN, you must create firewall
# rules for the the TUN/TAP interface.
# On non-Windows systems, you can give
# an explicit unit number, such as tun0.
# On Windows, use "dev-node" for this.
# On most systems, the VPN will not function
# unless you partially or fully disable
# the firewall for the TUN/TAP interface.
;dev tap
dev tun
# Windows needs the TAP-Win32 adapter name
# from the Network Connections panel if you
# have more than one. On XP SP2 or higher,
# you may need to selectively disable the
# Windows firewall for the TAP adapter.
# Non-Windows systems usually don't need this.
;dev-node MyTap
# SSL/TLS root certificate (ca), certificate
# (cert), and private key (key). Each client
# and the server must have their own cert and
# key file. The server and all clients will
# use the same ca file.
#
# See the "easy-rsa" directory for a series
# of scripts for generating RSA certificates
# and private keys. Remember to use
# a unique Common Name for the server
# and each of the client certificates.
#
# Any X509 key management system can be used.
# OpenVPN can also use a PKCS #12 formatted key file
# (see "pkcs12" directive in man page).
# specify hardcoded paths to
ca keys /etc/openvpn/easy-rsa/keys/ca.crt # public key of the certificate authority
cert /etc/openvpn/easy-rsa/keys/mana.crt # public key of the server
key /etc/openvpn/easy-rsa/keys/mana.key # private key of the server
# Diffie hellman parameters.
# Generate your own with:
# openssl dhparam -out dh2048.pem 2048
# hardcode the path to the DH parameters
dh /etc/openvpn/easy-rsa/keys/dh2048.pem
# Network topology
# Should be subnet (addressing via IP)
# unless Windows clients v2.0.9 and lower have to
# be supported (then net30, ie a /30 per client)
# Defaults to net30 (not recommended)
; topology subnet
# Configure server mode and supply a VPN subnet
# for OpenVPN to draw client addresses from.
# The server will take 10.8.0.1 for itself,
# the rest will be made available to clients.
# Each client will be able to reach the server
# on 10.8.0.1. Comment this line out if you are
# ethernet bridging. See the man page for more info.
# by default the VPN network will be 10.8.0.X
server 10.8.0.0 255.255.255.0
# Maintain a record of client <-> virtual IP address
# associations in this file. If OpenVPN goes down or
# is restarted, reconnecting clients can be assigned
# the same virtual IP address from the pool that was
# previously assigned.
# by default the client will always have the same IP address assigned
ifconfig-pool-persist ipp.txt
# Configure server mode for ethernet bridging.
# You must first use your OS's bridging capability
# to bridge the TAP interface with the ethernet
# NIC interface. Then you must manually set the
# IP/netmask on the bridge interface, here we
# assume 10.8.0.4/255.255.255.0. Finally we
# must set aside an IP range in this subnet
# (start=10.8.0.50 end=10.8.0.100) to allocate
# to connecting clients. Leave this line commented
# out unless you are ethernet bridging.
;server-bridge 10.8.0.4 255.255.255.0 10.8.0.50 10.8.0.100
# Configure server mode for ethernet bridging
# using a DHCP-proxy, where clients talk
# to the OpenVPN server-side DHCP server
# to receive their IP address allocation
# and DNS server addresses. You must first use
# your OS's bridging capability to bridge the TAP
# interface with the ethernet NIC interface.
# Note: this mode only works on clients (such as
# Windows), where the client-side TAP adapter is
# bound to a DHCP client.
;server-bridge
# Push routes to the client to allow it
# to reach other private subnets behind
# the server. Remember that these
# private subnets will also need
# to know to route the OpenVPN client
# address pool (10.8.0.0/255.255.255.0)
# back to the OpenVPN server.
# we authorize the client to see the addresses of the local network
;push "route 192.168.10.0 255.255.255.0"
;push "route 192.168.20.0 255.255.255.0"
push "route 192.168.1.0 255.255.255.0"
# To assign specific IP addresses to specific
# clients or if a connecting client has a private
# subnet behind it that should also have VPN access,
# use the subdirectory "ccd" for client-specific
# configuration files (see man page for more info).
# EXAMPLE: Suppose the client
# having the certificate common name "Thelonious"
# also has a small subnet behind his connecting
# machine, such as 192.168.40.128/255.255.255.248.
# First, uncomment out these lines:
# we authorize the client with the address 192.168.43.X
client-config-dir ccd
route 192.168.43.0 255.255.255.0
# Then create a file ccd/Thelonious with this line:
# iroute 192.168.40.128 255.255.255.248
# This will allow Thelonious' private subnet to
# access the VPN. This example will only work
# if you are routing, not bridging, ie you are
# using "dev tun" and "server" directives.
# EXAMPLE: Suppose you want to give
# Thelonious a fixed VPN IP address of 10.9.0.1.
# First uncomment out these lines:
;client-config-dir ccd
;route 10.9.0.0 255.255.255.252
# Then add this line to ccd/Thelonious:
# ifconfig-push 10.9.0.1 10.9.0.2
# Assume that you want to enable different
# firewall access policies for different groups
# of clients. There are two methods:
# (1) Run multiple OpenVPN daemons, one for each
# group, and firewall the TUN/TAP interface
# for each group/daemon appropriately.
# (2) (Advanced) Create a script to dynamically
# modify the firewall in response to access
# from different clients. See man
# page for more info on learn-address script.
;learn-address ./script
# If enabled, this directive will configure
# all clients to redirect their default
# network gateway through the VPN, causing
# all IP traffic such as web browsing and
# and DNS lookups to go through the VPN
# (The OpenVPN server machine may need to NAT
# or bridge the TUN/TAP interface to the internet
# in order for this to work properly).
# commented line to not redirect the
# internet flow from the client to the vpn server
;push "redirect-gateway def1 bypass-dhcp"
# Certain Windows-specific network settings
# can be pushed to clients, such as DNS
# or WINS server addresses. CAVEAT:
# http://openvpn.net/faq.html#dhcpcaveats
# The addresses below refer to the public
# DNS servers provided by opendns.com.
# I comment these lines to
avoid using
# VPN DNS on the client
;push "dhcp-option DNS 208.67.220.220"
# Uncomment this directive to allow different
# clients to be able to "see" each other.
# By default, clients will only see the server.
# To force clients to only see the server, you
# will also need to appropriately firewall the
# server's TUN/TAP interface.
;client-to-client
# Uncomment this directive if multiple clients
# might connect with the same certificate/key
# files or common names. This is recommended
# only for testing purposes. For production use,
# each client should have its own certificate/key
# pair.
#
# IF YOU HAVE NOT GENERATED INDIVIDUAL
# CERTIFICATE/KEY PAIRS FOR EACH CLIENT,
# EACH HAVING ITS OWN UNIQUE "COMMON NAME",
# UNCOMMENT THIS LINE OUT.
;duplicate-cn
# The keepalive directive causes ping-like
# messages to be sent back and forth over
# the link so that each side knows when
# the other side has gone down.
# Ping every 10 seconds, assume that remote
# peer is down if no ping received during
# a 120 second time period.
keepalive 10 120
# For extra security beyond that provided
# by SSL/TLS, create an "HMAC firewall"
# to help block DoS attacks and UDP port flooding.
#
# Generate with:
# openvpn --genkey --secret ta.key
# #
The server and each client must have
# a copy of this key.
# The second parameter should be '0'
# on the server and '1' on the clients.
# indicate the hard path
tls-auth /etc/openvpn/easy-rsa/keys/ta.key 0 # This file is secret
# Select a cryptographic cipher.
# This config item must be copied to
# the client config file as well.
# Note that v2.4 client/server will automatically
# negotiate AES-256-GCM in TLS mode.
# See also the ncp-cipher option in the manpage
cipher AES-256-CBC
# Enable compression on the VPN link and push the
# option to the client (v2.4+ only, for earlier
# versions see below)
compress lz4-v2
push "compress lz4-v2"
# For compression compatible with older clients use comp-lzo
# If you enable it here, you must also
# enable it in the client config file.
;comp-lzo
# The maximum number of concurrently connected
# clients we want to allow.
;max-clients 100
# It's a good idea to reduce the OpenVPN
# daemon's privileges after initialization.
#
# You can uncomment this out on
# non-Windows systems.
# to uncomment for more security
user openvpn
group openvpn
# The persistent options will try to avoid
# accessing certain resources on restart
# that may no longer be accessible because
# of the privilege downgrade.
persist-key
persist-tun
# Output a short status file showing
# current connections, truncated
# and rewritten every minute.
status openvpn-status.log
# By default, log messages will go to the syslog (or
# on Windows, if running as a service, they will go to
# the "\Program Files\OpenVPN\log" directory).
# Use log or log-append to override this default.
# "log" will truncate the log file on OpenVPN startup,
# while "log-append" will append to it. Use one
# or the other (but not both).
;log openvpn.log
;log-append openvpn.log
# Set the appropriate level of log
# file verbosity.
#
# 0 is silent, except for fatal errors
# 4 is reasonable for general usage
# 5 and 6 can help to debug connection problems
# 9 is extremely verbose
# value set to 4
verb 4
# Silence repeating messages. At most 20
# sequential messages of the same message
# category will be output to the log.
;mute 20
# Notify the client that when the server restarts so it
# can automatically reconnect.
explicit-exit-notify 1
Note that lines starting with ; are comments. The following points from the server configuration file should be noted:
- the local address of the server on the local network
local 192.168.1.11
- the VPN server port
port 1194
- the default network VPN 10.8.0.X
server 10.8.0.0 255.255.255.0
- by default clients will always have the same IP address assigned by the VPN
ifconfig-pool-persist ipp.txt
- Clients are allowed to access workstations on the local network 192.168.1.X
push "route 192.168.1.0 255.255.255.0"
- We route the client with its private address 192.168.43.X, this corresponds to the local address of my client assigned by the 4G mobile
client-config-dir
ccd
route 192.168.43.0
255.255.255.0
- we comment these lines so as not to use the VPN DNS by the client who will continue to use its default DNS
;push
"dhcp-option DNS 208.67.222.222"
;push "dhcp-option DNS
208.67.220.220"
- we comment this line so that the client's internet flow does not go through the VPN
;push "redirect-gateway def1 bypass-dhcp"
- we uncomment these lines so that the openvpn user is the owner of the openvpn daemon and not root with the minimum privileges
user openvpn
group openvpn
now I will create the directory /etc/openvpn/ccd which will contain the tetiaroa file which will contain
iroute 192.168.43.0 255.255.255.0
Configuring routes and firewall
In terms of routes, it will be quite minimalistic because we will not activate the IP masquerade on the server so that the client can access the Internet via VPN. However, the shorewall firewall will have to be configured. The topology of my network is recalled in the diagram presented above. On my box, I redirected the connections to port 1194 to my router, on my router they are redirected to my mana server with the address 192.168.1.11 which, as a reminder, has a network interface designated by eno2.
The following files will be modified (additions in italics)
contents of /etc/shorewall/interfaces
lan eno2 -
vpn tun0 -
contents of /etc/shorewall/policy
fw lan ACCEPT
vpn all ACCEPT
all all REJECT info
contents of /etc/shorewall/rules
ACCEPT fw lan icmpACCEPT lan:192.168.1.0/24 fw tcp 22,25,80,111,143,389,443,465
ACCEPT lan:192.168.1.0/24 fw udp 111
ACCEPT lan:192.168.1.0/24 fw icmp
DNS(ACCEPT) fw lan
ACCEPT lan fw:192.168.1.11 udp 1194
ACCEPT all vpn all
contents of /etc/shorewall/tunnels
openvpn:1194 lan 0.0.0.0/0 vpn
contents of /etc/shorewall/zones
fw firewall
lan ipv4
vpn ipv4
systemctl
stop shorewall
systemctl start shorewall
Client Installation and Configuration
For the installation, it's like for the server, you will have to install the openvpn package , under mageia
urpmi openvpn
On the server (and not the client) we will create the file /etc/openvpn/easy-rsa/keys/Default.txt which will contain
client
dev tun
proto udp
remote mana-noip 1194
resolv-retry infinite
nobind
persist-key
persist-tun
mute-replay-warnings
ns-cert-type server
key-direction 1
cipher AES-256-CBC
compress lz4-v2
verb 1
mute 20
script-security 2
bash MakeOpenVPN.sh
here is the result
Enter the
name of an existing client:
tetiaroa
Public key found: tetiaroa
Private key found:
tetiaroa.3des.key
CA public key found:
ca.crt
tls-auth private key
found: ta.key
Done! tetiaroa.ovpn
generated successfully.
MakeOpenVPN.sh: line 73:
Step: command not found
This will create a complete configuration file tetiaroa.ovpn including the configuration and keys needed to connect. This file must be placed in the client's /etc/openvpn directory , you will need to make sure to transfer this file securely from the server to the client.
Launching and running OpenVPN
Now we go back to the server. The openvpn service was installed by default when installing the package but it is not active by default, to activate it you will have to type the command (under mageia, to be adapted according to your distribution)systemctl enable openvpn@server.service
here is the result
systemctl
enable openvpn@server.service
Created symlink
/etc/systemd/system/openvpn.target.wants/openvpn@server.service
→ /usr/lib/systemd/system/openvpn@.service.
To launch openvpn we will type
systemctl start openvpn@server.service
here is the result with journalctl and verbose mode 4
juil. 24 11:21:56 mana.kervao.fr systemd[1]: Starting OpenVPN
Robust And Highly Flexible Tunneling Application (Config:
server)...
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]: Current
Parameter Settings:
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
config = 'server.conf'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]: mode
= 1
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
persist_config = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
persist_mode = 1
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
show_ciphers = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
show_digests = DISABLED
juil. 24 11:21:56 mana.kervao.fr audit[1]: SERVICE_START pid=1
uid=0 auid=4294967295 ses=4294967295 msg='unit=openvpn@server
comm="systemd" exe="/usr/lib/systemd/systemd" hostname=? addr=?
terminal=? res=success'
juil. 24 11:21:56 mana.kervao.fr systemd[1]: Started OpenVPN
Robust And Highly Flexible Tunneling Application (Config:
server).
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
show_engines = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
genkey = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
key_pass_file = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
show_tls_ciphers = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
connect_retry_max = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]: Connection
profiles [0]:
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
proto = udp
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
local = '192.168.1.11'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
local_port = '1194'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
remote = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
remote_port = '1194'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
remote_float = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
bind_defined = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
bind_local = ENABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
bind_ipv6_only = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
connect_retry_seconds = 5
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
connect_timeout = 120
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
socks_proxy_server = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
socks_proxy_port = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
tun_mtu = 1500
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
tun_mtu_defined = ENABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
link_mtu = 1500
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
link_mtu_defined = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
tun_mtu_extra = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
tun_mtu_extra_defined = DISABLED
juil. 24 11:21:56 mana.kervao.fr kernel: audit: type=1130
audit(1627118516.126:193602): pid=1 uid=0 auid=4294967295
ses=4294967295 msg='unit=openvpn@server comm="systemd"
exe="/usr/lib/systemd/systemd" hostname=? addr=? terminal=?
res=success'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
mtu_discover_type = -1
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
fragment = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
mssfix = 1450
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
explicit_exit_notification = 1
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]: Connection
profiles END
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
remote_random = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ipchange = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]: dev
= 'tun'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
dev_type = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
dev_node = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
lladdr = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
topology = 1
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ifconfig_local = '10.8.0.1'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ifconfig_remote_netmask = '10.8.0.2'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ifconfig_noexec = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ifconfig_nowarn = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ifconfig_ipv6_local = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ifconfig_ipv6_netbits = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ifconfig_ipv6_remote = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
shaper = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
mtu_test = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
mlock = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
keepalive_ping = 10
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
keepalive_timeout = 120
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
inactivity_timeout = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ping_send_timeout = 10
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ping_rec_timeout = 240
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ping_rec_timeout_action = 2
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ping_timer_remote = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
remap_sigusr1 = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
persist_tun = ENABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
persist_local_ip = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
persist_remote_ip = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
persist_key = ENABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
passtos = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
resolve_retry_seconds = 1000000000
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
resolve_in_advance = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
username = 'openvpn'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
groupname = 'openvpn'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
chroot_dir = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
cd_dir = '/etc/openvpn/'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
writepid = '/run/openvpn/server.pid'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
up_script = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
down_script = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
down_pre = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
up_restart = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
up_delay = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
daemon = ENABLED
juil. 24 11:21:56 mana.kervao.fr systemd-networkd[605]: tun0:
Gained carrier
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
inetd = 0
juil. 24 11:21:56 mana.kervao.fr systemd-udevd[9494]:
link_config: autonegotiation is unset or enabled, the speed and
duplex are not writable.
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]: log
= DISABLED
juil. 24 11:21:56 mana.kervao.fr systemd-networkd[605]: tun0:
Gained IPv6LL
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
suppress_timestamps = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
machine_readable_output = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]: nice
= 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
verbosity = 4
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]: mute
= 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
gremlin = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
status_file = 'openvpn-status.log'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
status_file_version = 1
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
status_file_update_freq = 60
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]: occ
= ENABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
rcvbuf = 0
juil. 24 11:21:56 mana.kervao.fr systemd-udevd[9494]: Process
'net_create_ifcfg' failed with exit code 1.
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
sndbuf = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]: mark
= 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
sockflags = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
fast_io = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
comp.alg = 11
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
comp.flags = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
route_script = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
route_default_gateway = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
route_default_metric = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
route_noexec = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
route_delay = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
route_delay_window = 30
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
route_delay_defined = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
route_nopull = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
route_gateway_via_dhcp = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
allow_pull_fqdn = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
route 10.8.0.0/255.255.255.0/default (not set)/default (not set)
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
route 192.168.43.0/255.255.255.0/default (not set)/default (not
set)
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
management_addr = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
management_port = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
management_user_pass = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
management_log_history_cache = 250
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
management_echo_buffer_size = 100
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
management_write_peer_info_file = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
management_client_user = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
management_client_group = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
management_flags = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
shared_secret_file = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
key_direction = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ciphername = 'AES-256-CBC'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ncp_enabled = ENABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ncp_ciphers = 'AES-256-GCM:AES-128-GCM'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
authname = 'SHA1'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
prng_hash = 'SHA1'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
prng_nonce_secret_len = 16
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
keysize = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
engine = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
replay = ENABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
mute_replay_warnings = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
replay_window = 64
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
replay_time = 15
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
packet_id_file = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
use_iv = ENABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
test_crypto = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
tls_server = ENABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
tls_client = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
key_method = 2
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ca_file = '/etc/openvpn/easy-rsa/keys/ca.crt'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ca_path = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
dh_file = '/etc/openvpn/easy-rsa/keys/dh2048.pem'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
cert_file = '/etc/openvpn/easy-rsa/keys/mana.crt'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
extra_certs_file = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
priv_key_file = '/etc/openvpn/easy-rsa/keys/mana.key'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
pkcs12_file = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
cipher_list = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
cipher_list_tls13 = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
tls_cert_profile = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
tls_verify = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
tls_export_cert = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
verify_x509_type = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
verify_x509_name = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
crl_file = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ns_cert_type = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
remote_cert_ku[i] = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
remote_cert_ku[i] = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
remote_cert_ku[i] = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
remote_cert_ku[i] = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
remote_cert_ku[i] = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
remote_cert_ku[i] = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
remote_cert_ku[i] = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
remote_cert_ku[i] = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
remote_cert_ku[i] = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
remote_cert_ku[i] = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
remote_cert_ku[i] = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
remote_cert_ku[i] = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
remote_cert_ku[i] = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
remote_cert_ku[i] = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
remote_cert_ku[i] = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
remote_cert_ku[i] = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
remote_cert_eku = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ssl_flags = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
tls_timeout = 2
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
renegotiate_bytes = -1
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
renegotiate_packets = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
renegotiate_seconds = 3600
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
handshake_window = 60
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
transition_window = 3600
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
single_session = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
push_peer_info = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
tls_exit = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
tls_auth_file = '/etc/openvpn/easy-rsa/keys/ta.key'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
tls_crypt_file = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
server_network = 10.8.0.0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
server_netmask = 255.255.255.0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
server_network_ipv6 = ::
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
server_netbits_ipv6 = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
server_bridge_ip = 0.0.0.0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
server_bridge_netmask = 0.0.0.0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
server_bridge_pool_start = 0.0.0.0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
server_bridge_pool_end = 0.0.0.0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
push_entry = 'route 192.168.1.0 255.255.255.0'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
push_entry = 'compress lz4-v2'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
push_entry = 'route 10.8.0.1'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
push_entry = 'topology net30'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
push_entry = 'ping 10'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
push_entry = 'ping-restart 120'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ifconfig_pool_defined = ENABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ifconfig_pool_start = 10.8.0.4
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ifconfig_pool_end = 10.8.0.251
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ifconfig_pool_netmask = 0.0.0.0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ifconfig_pool_persist_filename = 'ipp.txt'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ifconfig_pool_persist_refresh_freq = 600
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ifconfig_ipv6_pool_defined = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ifconfig_ipv6_pool_base = ::
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ifconfig_ipv6_pool_netbits = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
n_bcast_buf = 256
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
tcp_queue_limit = 64
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
real_hash_size = 256
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
virtual_hash_size = 256
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
client_connect_script = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
learn_address_script = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
client_disconnect_script = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
client_config_dir = 'ccd'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
ccd_exclusive = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
tmp_dir = '/tmp'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
push_ifconfig_defined = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
push_ifconfig_local = 0.0.0.0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
push_ifconfig_remote_netmask = 0.0.0.0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
push_ifconfig_ipv6_defined = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
push_ifconfig_ipv6_local = ::/0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
push_ifconfig_ipv6_remote = ::
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
enable_c2c = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
duplicate_cn = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
cf_max = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
cf_per = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
max_clients = 1024
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
max_routes_per_client = 256
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
auth_user_pass_verify_script = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
auth_user_pass_verify_script_via_file = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
auth_token_generate = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
auth_token_lifetime = 0
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
port_share_host = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
port_share_port = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
client = DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]: pull
= DISABLED
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]:
auth_user_pass_file = '[UNDEF]'
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]: OpenVPN 2.4.9
x86_64-mageia-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL]
[MH/PKTINFO] [AEAD] built on Apr 28 2020
juil. 24 11:21:56 mana.kervao.fr openvpn[9490]: library
versions: OpenSSL 1.1.0l 10 Sep 2019, LZO 2.10
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]: Diffie-Hellman
initialized with 2048 bit key
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]: Outgoing Control
Channel Authentication: Using 160 bit message hash 'SHA1' for
HMAC authentication
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]: Incoming Control
Channel Authentication: Using 160 bit message hash 'SHA1' for
HMAC authentication
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]: TLS-Auth MTU
parms [ L:1622 D:1184 EF:66 EB:0 ET:0 EL:3 ]
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]: ROUTE_GATEWAY
192.168.1.1/255.255.255.0 IFACE=eno2 HWADDR=79:2e:cb:62:8f:ce
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]: TUN/TAP device
tun0 opened
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]: TUN/TAP TX queue
length set to 100
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]: do_ifconfig,
tt->did_ifconfig_ipv6_setup=0
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]:
/usr/sbin/ifconfig tun0 10.8.0.1 pointopoint 10.8.0.2 mtu 1500
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]: /usr/sbin/route
add -net 192.168.43.0 netmask 255.255.255.0 gw 10.8.0.2
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]: /usr/sbin/route
add -net 10.8.0.0 netmask 255.255.255.0 gw 10.8.0.2
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]: Data Channel MTU
parms [ L:1622 D:1450 EF:122 EB:406 ET:0 EL:3 ]
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]: Could not
determine IPv4/IPv6 protocol. Using AF_INET
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]: Socket Buffers:
R=[212992->212992] S=[212992->212992]
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]: UDPv4 link local
(bound): [AF_INET]192.168.1.11:1194
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]: UDPv4 link
remote: [AF_UNSPEC]
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]: GID set to
openvpn
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]: UID set to
openvpn
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]: MULTI:
multi_init called, r=256 v=256
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]: IFCONFIG POOL:
base=10.8.0.4 size=62, ipv6=0
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]:
ifconfig_pool_read(), in='tetiaroa,10.8.0.4', TODO: IPv6
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]: succeeded ->
ifconfig_pool_set()
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]: IFCONFIG POOL
LIST
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]:
tetiaroa,10.8.0.4
juil. 24 11:21:56 mana.kervao.fr openvpn[9491]: Initialization
Sequence Completed
You can get an idea of the server status by typing
systemctl status openvpn@server.service
here is the result
● openvpn@server.service - OpenVPN Robust And Highly Flexible Tunneling Application (Config: server)Loaded: loaded (/usr/lib/systemd/system/openvpn@.service; enabled; vendor preset: disabled)
Active: active (running) since Thu 2021-07-22 17:25:23 CEST; 48s ago
Process: 26145 ExecStart=/usr/sbin/openvpn --daemon --writepid /run/openvpn/server.pid --cd /etc/openvpn/ --config server.conf (code=exited, status=0/SUCCESS)
Main PID: 26146 (openvpn)
Tasks: 1 (limit: 4685)
Memory: 2.1M
CGroup: /system.slice/system-openvpn.slice/openvpn@server.service
└─26146 /usr/sbin/openvpn --daemon --writepid /run/openvpn/server.pid --cd /etc/openvpn/ --config server.conf
Jul 22 17:25:23 mana.kervao.fr openvpn[26146]: UDPv4 link remote: [AF_UNSPEC]
Jul 22 17:25:23 mana.kervao.fr openvpn[26146]: GID set to openvpn
Jul 22 17:25:23 mana.kervao.fr openvpn[26146]: UID set to openvpn
Jul 22 17:25:23 mana.kervao.fr openvpn[26146]: MULTI: multi_init called, r=256 v=256
Jul 22 17:25:23 mana.kervao.fr openvpn[26146]: IFCONFIG POOL: base=10.8.0.4 size=62, ipv6=0
Jul 22 17:25:23 mana.kervao.fr openvpn[26146]: ifconfig_pool_read(), in='tetiaroa,10.8.0.4', TODO: IPv6
Jul 22 17:25:23 mana.kervao.fr openvpn[26146]: succeeded -> ifconfig_pool_set()
Jul 22 17:25:23 mana.kervao.fr openvpn[26146]: IFCONFIG POOL LIST
Jul 22 17:25:23 mana.kervao.fr openvpn[26146]: tetiaroa,10.8.0.4
Jul 22 17:25:23 mana.kervao.fr openvpn[26146]: Initialization Sequence Completed
Now we see that the tunnel was created by typing on the server
ifconfig -a
we see the tun0 tunnel which has appeared
tun0:
flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu
1500
inet 10.8.0.1
netmask 255.255.255.255 destination 10.8.0.2
inet6
fe79::8e03:7e65:1ae7:933 prefixlen 64 scopeid
0x20<link>
unspec
00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen
100 (UNSPEC)
RX packets 0
bytes 0 (0.0 B)
RX errors 0
dropped 0 overruns 0 frame 0
TX packets 12
bytes 726 (726.0 B)
TX errors 0
dropped 0 overruns 0 carrier 0 collisions 0
The server has the address in the VPN network 10.8.0.1 as indicated in its configuration file.
Now we are going to launch the connection on the client side, so we go to the client and type
openvpn --config /etc/openvpn/tetiaroa.ovpn
here is the result
2021-07-23 17:06:29
WARNING: Compression for receiving enabled. Compression has
been used in the past to break encryption. Sent packets are
not compressed unless "allow-compression yes" is also set.
2021-07-23 17:06:29
DEPRECATED OPTION: --cipher set to 'AES-256-CBC' but missing
in --data-ciphers (AES-256-GCM:AES-128-GCM). Future OpenVPN
version will ignore --cipher for cipher negotiations. Add
'AES-256-CBC' to --data-ciphers or
change --cipher
'AES-256-CBC' to --data-ciphers-fallback 'AES-256-CBC' to
silence this warning.
2021-07-23 17:06:29
OpenVPN 2.5.0 x86_64-mageia-linux-gnu [SSL (OpenSSL)] [LZO]
[LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Nov 9
2020
2021-07-23 17:06:29
library versions: OpenSSL 1.1.1k 25 Mar 2021, LZO 2.10
2021-07-23 17:06:29
WARNING: --ns-cert-type is DEPRECATED. Use --remote-cert-tls
instead.
2021-07-23 17:06:29 NOTE:
the current --script-security setting may allow this
configuration to call user-defined scripts
🔐 Enter Private Key
Password:
***********
2021-07-23 17:06:36
WARNING: this configuration may cache passwords in memory --
use the auth-nocache option to prevent this
2021-07-23 17:06:37
TCP/UDP: Preserving recently used remote address:
[AF_INET]94.11.100.53:1194
2021-07-23 17:06:37 UDP
link local: (not bound)
2021-07-23 17:06:37 UDP
link remote: [AF_INET]94.11.100.53:1194
2021-07-23 17:06:38
[mana-noip] Peer Connection Initiated with
[AF_INET]94.11.100.53:1194
2021-07-23 17:06:39
WARNING: Compression for receiving enabled. Compression has
been used in the past to break encryption. Sent packets are
not compressed unless "allow-compression yes" is also set.
2021-07-23 17:06:39
TUN/TAP device tun0 opened
2021-07-23 17:06:39
net_iface_mtu_set: mtu 1500 for tun0
2021-07-23 17:06:39
net_iface_up: set tun0 up
2021-07-23 17:06:39
net_addr_ptp_v4_add: 10.8.0.6 peer 10.8.0.5 dev tun0
2021-07-23 17:06:39
/etc/openvpn/update-resolv-conf tun0 1500 1553 10.8.0.6
10.8.0.5 init
dhcp-option DNS
208.67.222.222
dhcp-option DNS
208.67.220.220
2021-07-23 17:06:39
Initialization Sequence Completed
You will need to enter the password entered earlier when generating the client key. Note the address 94.11.100.53 which corresponds to the real IP address of the server on the Internet.
There too by typing
ifconfig -a
we see the tunnel that has been put in place
tun0:
flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST>
mtu 1500
inet 10.8.0.6
netmask 255.255.255.255 destination 10.8.0.5
inet6
fe79::fe30:bced:5d5e:d40e prefixlen 64 scopeid
0x20<link>
unspec
00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen
500 (UNSPEC)
RX packets 224
bytes 52524 (51.2 KiB)
RX errors 0
dropped 0 overruns 0 frame 0
TX packets 4433
bytes 413548 (403.8 KiB)
TX errors 0
dropped 0 overruns 0 carrier 0 collisions 0
The client ends up with the address 10.8.0.6 on the VPN network. And this is what it looks like on the server side
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]: MULTI:
multi_create_instance called
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
78.203.244.46:52136 Re-using SSL/TLS context
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
78.203.244.46:52136 LZ4v2 compression initializing
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
78.203.244.46:52136 Control Channel MTU parms [ L:1622 D:1184
EF:66 EB:0 ET:0 EL:3 ]
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
78.203.244.46:52136 Data Channel MTU parms [ L:1622 D:1450
EF:122 EB:406 ET:0 EL:3 ]
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
78.203.244.46:52136 Local Options String (VER=V4): 'V4,dev-type
tun,link-mtu 1558,tun-mtu 1500,proto UDPv4,comp-lzo,keydir
0,cipher AES-256-CBC,auth SHA1,keysize 256,tls-auth,key-method
2,tls-server'
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
78.203.244.46:52136 Expected Remote Options String (VER=V4):
'V4,dev-type tun,link-mtu 1558,tun-mtu 1500,proto
UDPv4,comp-lzo,keydir 1,cipher AES-256-CBC,auth SHA1,keysize
256,tls-auth,key-method 2,tls-client'
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
78.203.244.46:52136 TLS: Initial packet from
[AF_INET]78.203.244.46:52136, sid=8fd78fcb 9aca764b
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
78.203.244.46:52136 VERIFY OK: depth=1, C=FR, ST=Bretagne,
L=BreizhCity, O=Funix, OU=funix, CN=mana-noip, name=mana,
emailAddress=olivier.hoarau@funix.org
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
78.203.244.46:52136 VERIFY OK: depth=0, C=FR, ST=Bretagne,
L=BreizhCity, O=Funix, OU=funix, CN=tetiaroa, name=tetiaroa,
emailAddress=olivier.hoarau@funix.org
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
78.203.244.46:52136 peer info: IV_VER=2.5.0
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
78.203.244.46:52136 peer info: IV_PLAT=linux
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
78.203.244.46:52136 peer info: IV_PROTO=6
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
78.203.244.46:52136 peer info: IV_NCP=2
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
78.203.244.46:52136 peer info:
IV_CIPHERS=AES-256-GCM:AES-128-GCM:AES-256-CBC
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
78.203.244.46:52136 peer info: IV_LZ4=1
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
78.203.244.46:52136 peer info: IV_LZ4v2=1
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
78.203.244.46:52136 peer info: IV_LZO=1
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
78.203.244.46:52136 peer info: IV_COMP_STUB=1
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
78.203.244.46:52136 peer info: IV_COMP_STUBv2=1
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
78.203.244.46:52136 peer info: IV_TCPNL=1
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
78.203.244.46:52136 Control Channel: TLSv1.2, cipher TLSv1.2
ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
78.203.244.46:52136 [tetiaroa] Peer Connection Initiated with
[AF_INET]78.203.244.46:52136
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
tetiaroa/78.203.244.46:52136 OPTIONS IMPORT: reading client
specific options from: ccd/tetiaroa
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
tetiaroa/78.203.244.46:52136 MULTI_sva: pool returned
IPv4=10.8.0.6, IPv6=(Not enabled)
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
tetiaroa/78.203.244.46:52136 MULTI: Learn: 10.8.0.6 ->
tetiaroa/78.203.244.46:52136
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
tetiaroa/78.203.244.46:52136 MULTI: primary virtual IP for
tetiaroa/78.203.244.46:52136: 10.8.0.6
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
tetiaroa/78.203.244.46:52136 MULTI: internal route
192.168.43.0/24 -> tetiaroa/78.203.244.46:52136
juil. 24 12:27:46 mana.kervao.fr openvpn[4166]:
tetiaroa/78.203.244.46:52136 MULTI: Learn: 192.168.43.0/24 ->
tetiaroa/78.203.244.46:52136
juil. 24 12:27:47 mana.kervao.fr openvpn[4166]:
tetiaroa/78.203.244.46:52136 PUSH: Received control message:
'PUSH_REQUEST'
juil. 24 12:27:47 mana.kervao.fr openvpn[4166]:
tetiaroa/78.203.244.46:52136 SENT CONTROL [tetiaroa]:
'PUSH_REPLY,route 192.168.1.0 255.255.255.0,dhcp-option DNS
208.67.222.222,dhcp-option DNS 208.67.220.220,compress
lz4-v2,route 10.8.0.1,topology net30,ping 10,ping-restart
120,ifconfig 10.8.0.6 10.8.0.5,peer-id 0,cipher AES-256-GCM'
(status=1)
juil. 24 12:27:47 mana.kervao.fr openvpn[4166]:
tetiaroa/78.203.244.46:52136 Data Channel: using negotiated
cipher 'AES-256-GCM'
juil. 24 12:27:47 mana.kervao.fr openvpn[4166]:
tetiaroa/78.203.244.46:52136 Data Channel MTU parms [ L:1550
D:1450 EF:50 EB:406 ET:0 EL:3 ]
juil. 24 12:27:47 mana.kervao.fr openvpn[4166]:
tetiaroa/78.203.244.46:52136 Outgoing Data Channel: Cipher
'AES-256-GCM' initialized with 256 bit key
juil. 24 12:27:47 mana.kervao.fr openvpn[4166]:
tetiaroa/78.203.244.46:52136 Incoming Data Channel: Cipher
'AES-256-GCM' initialized with 256 bit key
We find the address 78.203.244.46 which corresponds to the IP address of my 4G mobile on the internet.
Now from the client I can "ping" the server with its local network name ( mana in my example). The ip r command on the client will give
default via 192.168.43.1
dev wlp3s0 proto dhcp metric 600
10.8.0.1 via 10.8.0.5 dev
tun0 proto static metric 50
10.8.0.5 dev tun0 proto
kernel scope link src 10.8.0.6 metric 50
94.11.100.53 via
192.168.43.1 dev wlp3s0 proto static metric 600
192.168.1.0/24 via
10.8.0.5 dev tun0 proto static metric 50
192.168.43.0/24 dev wlp3s0
proto kernel scope link src 192.168.43.70 metric 600
192.168.43.1 dev wlp3s0
proto static scope link metric 600
The client's wifi interface being wlp3s0 and for the record
- 10.8.0.1 is the IP address of the VPN server on the VPN
- 10.8.0.6 is the IP address of the VPN client on the VPN
- 94.11.199.53 is the real IP address of the VPN server on the internet
- 192.168.1.0 denotes the private local network
- 192.168.43.0 refers to the private local network where the VPN client is located
- 192.166.43.70 is the IP address of the VPN client on the VPN client's private network
- 192.168.43.1 is the gateway
of the VPN client's private LAN
To mount an NFS directory from the server to the client, I added the following line to the server's /etc/hosts file
10.8.0.6 tetiaroa-vpn.kervao.fr tetiaroa-vpn
assuming that the assigned address remains fixed (this is configured in the server configuration file)
then in the /etc/exports file I added tetiaroa-vpn and took it into account with exportfs -a and that's it, we have access to all the network shares remotely via the VPN.
It will probably be necessary to modify the shorewall configuration in this way
in the /etc/shorewall/interfaces file we add the line
vpn tun0 -
in the file /etc/shorewall/zones we add
vpn ipv4
and in the file /etc/shorewall/rules
ACCEPT all vpn all
VPN Graphical Clients
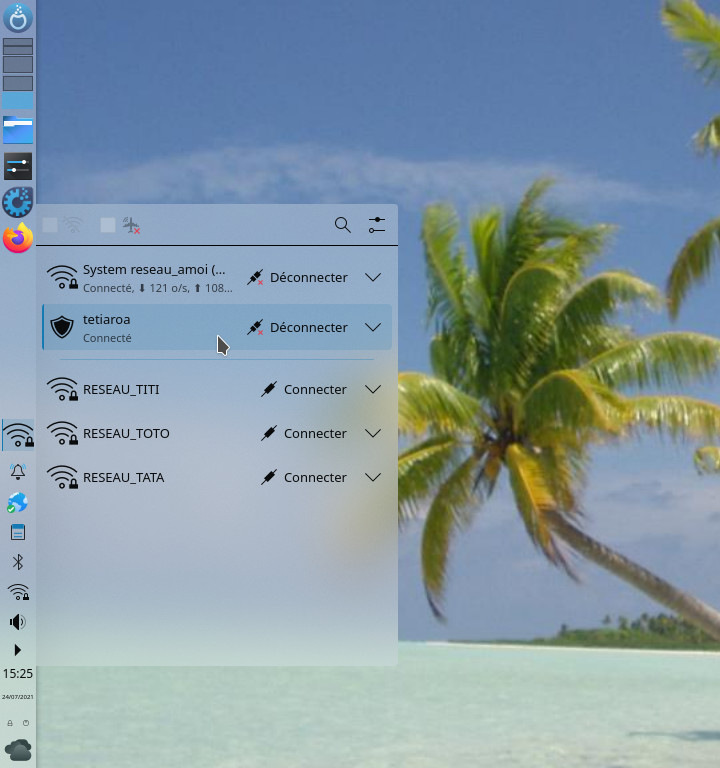
You can also use a VPN client with a graphical interface, this page lists a number of them. For those on mageia we can turn to drakvpn. For my part I chose NetworkManager which can be found on any distribution which allows you to directly take into account the tetiaroa.ovpn client file
Under plasma when you click on the configuration parameters at the Connections level , I click on the + to create a new connection then Import a VPN connection...
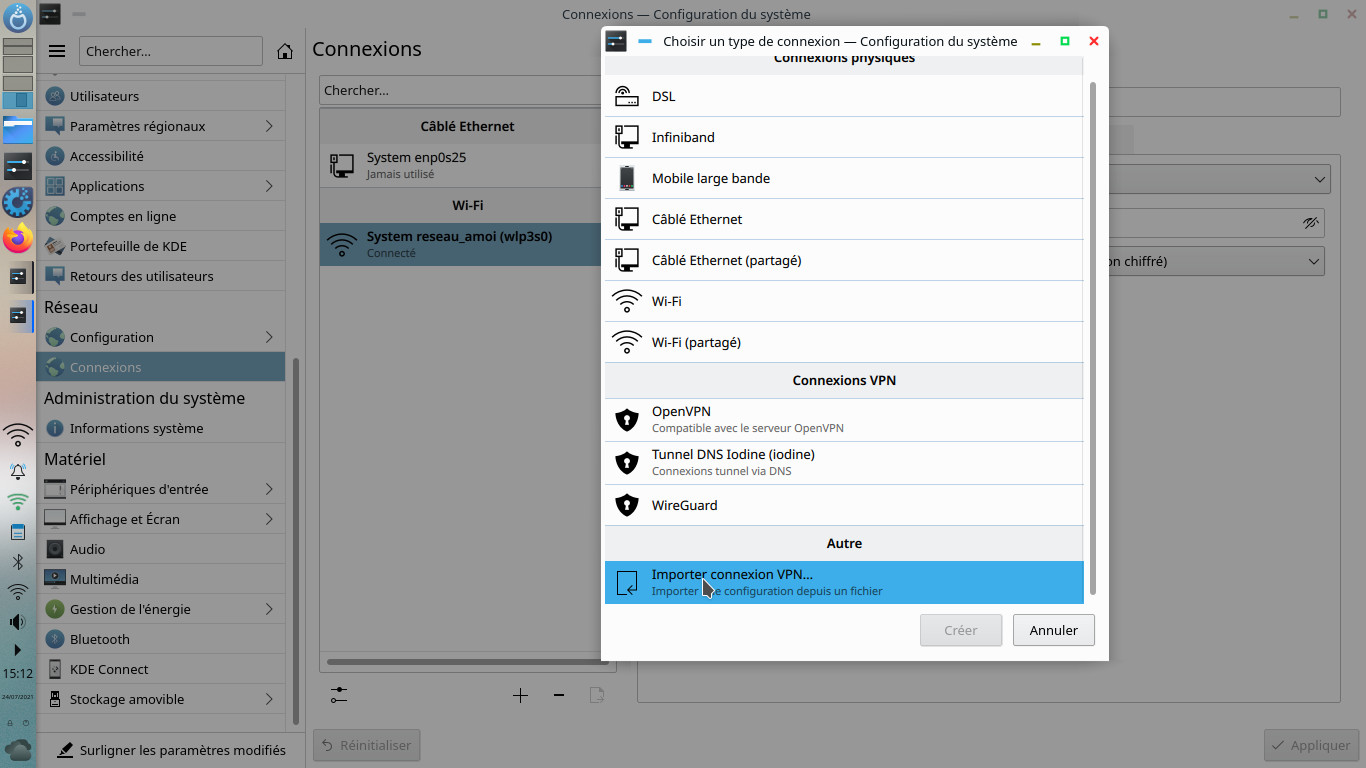
I designate my file /etc/openvpn/tetiaroa.ovpn the different fields are entered automatically and all you have to do is enter the password.
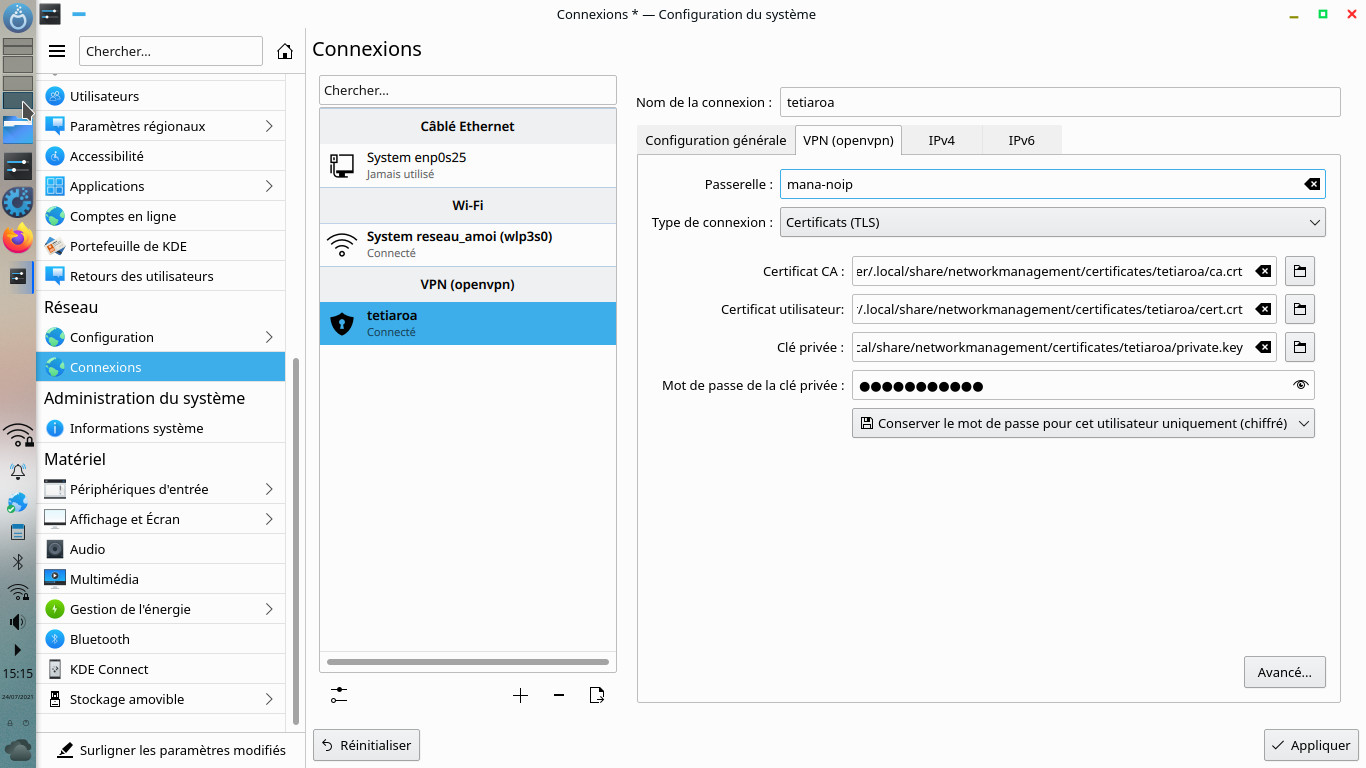
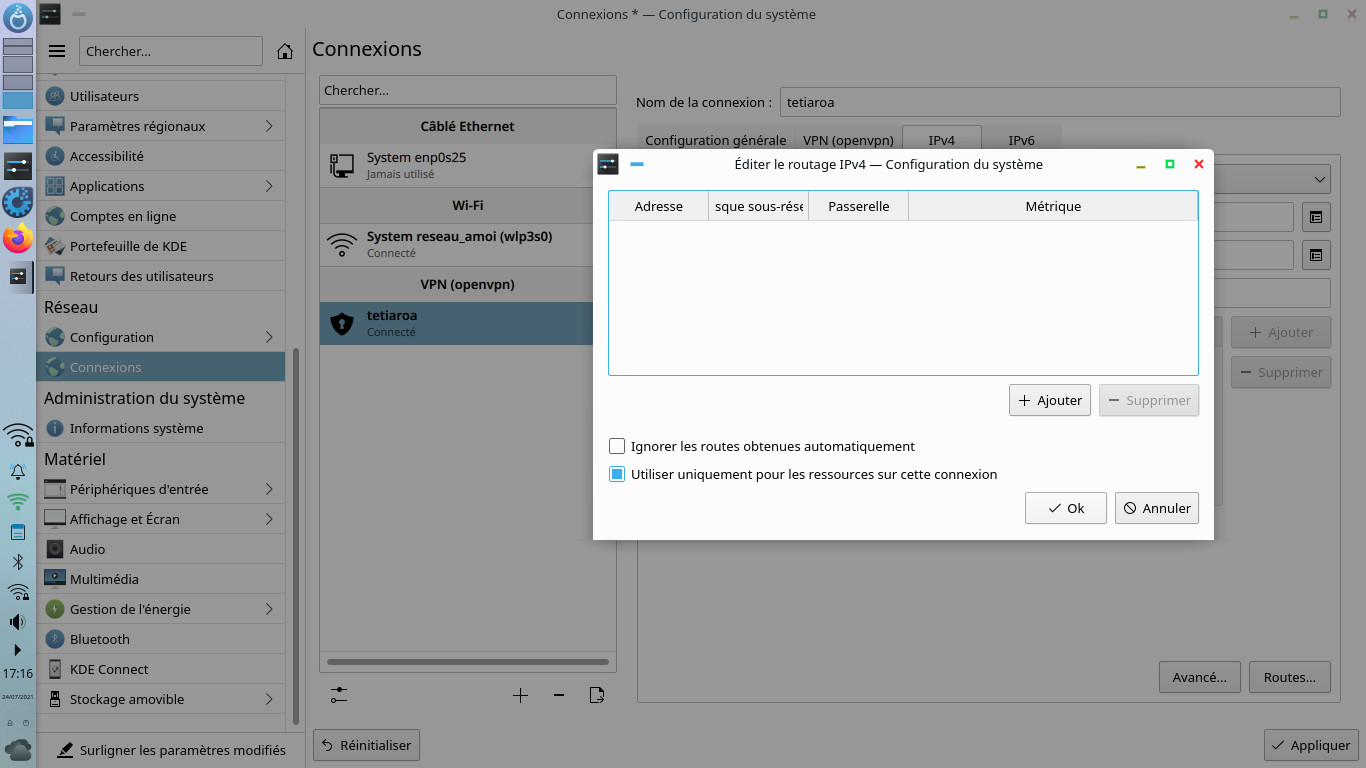
That's not all, you will have to click on the IPv4 tab then Routes... and check the box Use only for resources on this connection, otherwise all the internet flow will still go to the VPN tunnel.
The VPN network is also accessible from the Dashboard applet
| [ Back to FUNIX home page ] |
 Welcome
Welcome Linux
Linux Unix
Unix Download
Download