Last modified July 31,
2024
Managing mail transport with sendmail
This site has been automatically translated with Google Translate from this original page written in french, there may be some translation errors
Presentation
Why bother configuring sendmail, for the glory? Some say that as long as you haven't tried to configure sendmail, you're not a real system administrator... Let's say that sendmail is a tool (MTA mail transport agent to be precise) that allows you to manage the reception and sending of mails and to apply certain antispam and antivirus filters transparently and automatically. To summarize, here is how sendmail fits into an architecture for sending and receiving mails.
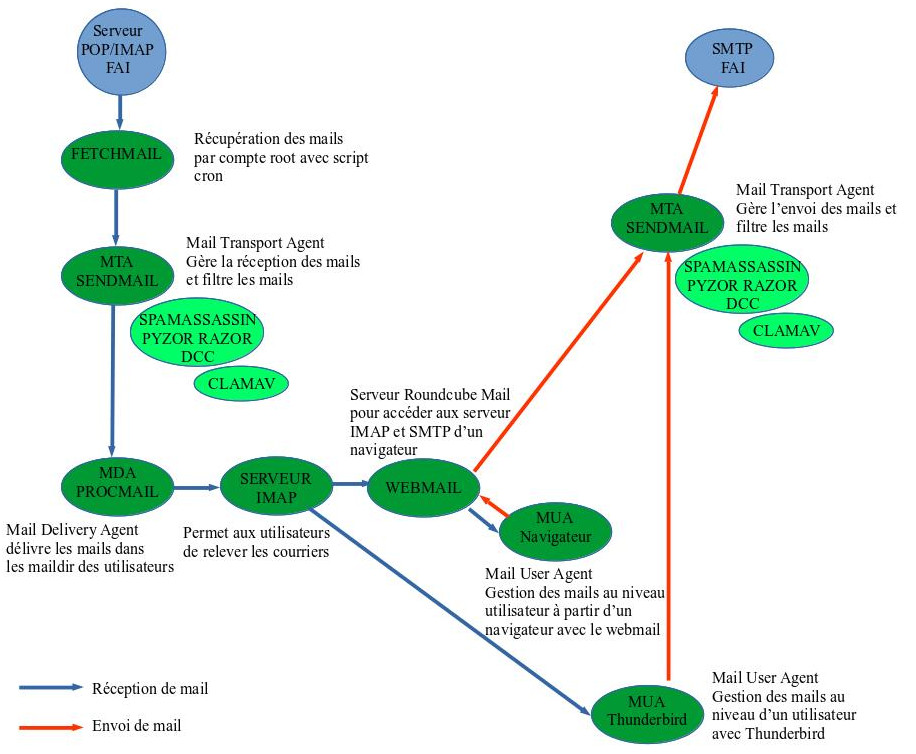
For receiving emails and installing POP, IMAP and webmail servers, please consult this page, for antispam and antivirus it's here.
There is now postfix which is apparently simpler and more secure, it is widely documented on the ne. As the configurations under sendmail at the moment are rather rare, I chose to be the last of the mohicans.
Facility
First of all, to install sendmail, we will simply use the distribution package.urpmi sendmail
If postfix causes conflict problems, force its uninstallation like this
rpm -e --nodeps postfix
Then try installing sendmail again . You will still need the following packages
sendmail-cf
m4
And possibly the sendmail-doc documentation package. Note that you can always find the reference doc on the sendmail website.
Configuration
For a Mageia I then created a file /usr/share/sendmail-cf/cf/config.mc which looks like this:include(`../m4/cf.m4')dnl
OSTYPE(`linux')dnl
FEATURE(redirect)dnl
FEATURE(nocanonify)dnl
FEATURE(always_add_domain)dnl
FEATURE(local_procmail)dnl
GENERICS_DOMAIN(machine.domaine.fr machine localhost)
FEATURE(genericstable)
FEATURE(masquerade_envelope)dnl
FEATURE(relay_entire_domain)dnl
FEATURE(accept_unresolvable_domains)dnl
define(`confDOMAIN_NAME',`ppp.fai.fr')dnl
define(`SMTP_MAILER_FLAGS',`e9')dnl
define(`confCON_EXPENSIVE', `True')dnl
define(`confME_TOO', `True')dnl
define(`confCF_VERSION', `Commentaire quelconque')dnl
define(`confCOPY_ERRORS_TO', `Postmaster')dnl
define(`confDEF_CHAR_SET', `UTF-8')dnl
define(`confMIME_FORMAT_ERRORS', `True')dnl
define(`SMART_HOST', `smtp8:[mail.fai.fr]')dnl
define(`confRECEIVED_HEADER', `from fai.fr
by fai.fr ($v/$Z)$?r with $r$. id $i$?u
for $u; $|;
$.$b')
define(`confTO_QUEUEWARN', `24h')dnl
MAILER(local)
MAILER(smtp)
Kpirateo hash -o /etc/mail/pirateo
LOCAL_RULE_0
R$+ < @ $+ > $* $: < $(pirateo $1 @ $2 $: $) > $1 < @ $2 > $3
R< $+ > $+ < @ $+ > $* $@ $>97 $1
R<> $+ < @ $+ > $* $: $1 < @ $2 > $3^^^^^^ tabulation unique à cet endroit, ailleurs un simple espace
The FEATURE(relay_entire_domain)
allows sendmail to accept
emails from workstations on your private network belonging to
your private domain, without this parameter when sending
emails, you would have an error message on Windows PCs like
"Relaying denied".
I also added FEATURE(accept_unresolvable_domains) because
without it if the Linux PC is offline there is no way to send
an email from a Windows PC to the Linux PC, on the other hand
as soon as you go online this parameter becomes completely
useless. I don't really understand why but I suspect a DNS
story behind this.
ATTENTION : single tab in last three lines.
NOTE : For an email to be sent locally to the toto account, you must type toto@machine or toto@machine.domain.fr as the destination email (without the domain), with machine being the name of your sendmail server and domain.fr being the name of your domain. If you enter toto@domain.fr, the email will be sent to the ISP before returning to the local network, even if domain.fr is defined in the GENERICSTABLE variable.
I also added define(`confDOMAIN_NAME',...) and define(`confRECEIVED_HEADER',...) refer to the paragraph masking domains.
Then we create a file / etc/mail/genericstable, which contains these lines:
toto: toto.nom@fai.frThis file matches local addresses with "official" addresses.
tata: tata.nom@fai.fr
Be careful, you must put a tab between the : and the address.
The line define(`confCF_VERSION', `Any comment') allows you to add any comment in the header of emails (see below).
To take into account the modification of this file, you must then type:
sendmail -bi -oA/etc/mail/genericstable
We then create a file / etc/mail/pirateo, in which you will put:
toto.nom@fai.fr toto
tata.nom@fai.fr tata
Then to generate the file in the correct format, type:
makemap hash /etc/mail/pirateo < /etc/mail/pirateo
This file will have the opposite effect of /etc/mail/generistable, it transforms the recipient address toto.nom@fai.fr into toto if the recipient is a local user, to prevent the mail from going to the fai. My /etc/hosts file starts with the following line
127.0.0.1 localhost localhost.localdomainDon't forget to add your stations from your private network with the FQDN (Fully qualified domain name), so that gives us this:
127.0.0.1 localhost localhost.localdomain
192.168.13.10 machine.domaine.fr machine
192.168.13.11 windows.domaine.fr windows
192.168.13.12 mac.domaine.fr mac
windows and mac being two machines of your private network, the IP addresses are given for information purposes only. The SMTP servers of ISPs (or others) now generally ask for a password to be able to access them in this case we will add the following line in the config.mc file
FEATURE(`authinfo',`hash /etc/mail/auth/clientinfo.db')dnl
we create the file /etc/mail/auth/clientinfo containing
AuthInfo:smtp.fai.net
"U:olivier.hoarau@funix.org" "I:olivier.hoarau@funix.org"
"P:mon-password" "M:PLAIN"
AuthInfo:
"U:olivier.hoarau@funix.org" "P:mon-password" "M:PLAIN"
we will create the file in the correct format by typing
makemap -r hash /etc/mail/auth/clientinfo.db < /etc/mail/auth/clientinfo
WARNING : if sendmail blocks the boot of the machine, it may come precisely from the fact that we have not modified the first line of /etc/hosts, sendmail cannot find the name of the machine and goes into a search that by default lasts 3 minutes. Furthermore, it can cause name resolution problems on the Linux machine in offline mode, to solve these problems while keeping the line in question unchanged, refer to the page installing a DNS server.
To rebuild the sendmail configuration file, type the command:
cd
/usr/share/sendmail-cf/cf/
m4 config.mc
> /etc/mail/sendmail.cf
Change (optionally) the
rights of this file:
chmod 600 /etc/mail/sendmail.cf
That's it, it's over
To restart everything, you must first kill sendmail if it is running, to do this:
systemctl stop sendmail
Then to reread the configuration file
sendmail -bd -os
if you get these errors554 /etc/sendmail.cf: line
51: unknown configuration line "
"
In fact, you just have to edit /etc/mail/sendmail.cf and delete a few empty lines at line 51, so that everything is back in order, type the command sendmail -bd -os again.
This is what systemctl status sendmail gives
sendmail.service - Sendmail
Mail Transport Agent
Loaded: loaded
(/usr/lib/systemd/system/sendmail.service; enabled)
Active: active
(running) since Sun 2015-10-04 20:59:56 CEST; 11min ago
Process: 1665
ExecStart=/bin/sh -c exec /usr/sbin/sendmail.sendmail
$DAEMONOPTIONS -bd $(if [ -n "$QUEUE" ]; then echo -q$QUEUE;
fi) (code=exited, status=0/SUCCESS)
Process: 1657
ExecStartPre=/usr/bin/make -C /etc/mail -s (code=exited,
status=0/SUCCESS)
Process: 1653
ExecStartPre=/usr/bin/newaliases (code=exited,
status=0/SUCCESS)
Main PID: 1667
(sendmail.sendma)
CGroup:
/system.slice/sendmail.service
à½1667 sendmail: accepting connections
Oct 04 20:59:55
mana.kervao.fr sendmail[1653]: alias database /etc/aliases
rebuilt by root
Oct. 04 20:59:55
mana.kervao.fr newaliases[1653]: /etc/aliases: 14 aliases,
longest 10 bytes, 152 bytes total
Oct. 04 20:59:55
mana.kervao.fr sendmail[1653]: /etc/aliases: 14 aliases,
longest 10 bytes, 152 bytes total
Oct 04 20:59:56
mana.kervao.fr sendmail[1667]: starting daemon (8.15.1):
SMTP+queueing@01:00:00
Operating principle
For information, all outgoing mail is waiting in the /var/spool/mqueue directory, incoming mail is in /var/spool/mail with the name of the recipient on the machine as the name.ATTENTION : /var/spool/mail must have drwxrwsr-x ( chmod g+s mail )
under /var/spool under mageia this is what I get when I type ll in a shelldrwxrwx--- 2 mail mail 4096 Oct 15 04:02 clientmqueue/
drwxrwsr-x 5 root mail 4096 Oct 15 12:23 mail/
drwxr-x--- 2 root mail 4096 Oct 15 12:01 mqueue/
To send the mail, once connected you must type:
/usr/sbin/sendmail -q -vThe -v option is the "verbose" option. To view the messages in the queue, you can type:
mailq
Configure sendmail to use an encrypted connection via SSL/TLS
The problem with the configuration presented above is that the password circulates in clear text between your clients and the server, we will encrypt them using SSL/TLS. First of all we will install a root certificate that identifies a local certification authority (CA for Certification Authority) which then validates the certificates of the servers that will be used to encrypt the exchanges.
On my
Mageia it is the rootcerts package which will
install the root certificate under /etc/pki. On this basis, we will
create the certificate and the key for the sendmail server by successively
typing several commands in a shell by first placing
ourselves under /etc/pki .
The first command is a certificate request for the sendmail server and will generate an unsigned certificate ( sendmail_certreq.pem ) and a private key ( sendmail_key.pem ).
openssl req -nodes -new -x509 -keyout private/sendmail_key.pem -out sendmail_certreq.pem
here is the result
.............+....+........+......+.+.............+.+.....+.+..+......++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*....+.+.....+...+....++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*......+.......+..+...+....++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
...+......+.........+......++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*.+...+....++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
++++++++*.+..+.......+...++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:Fr
State or Province Name (full name) []:Breizland
Locality Name (eg, city) [Default City]:Brest
Organization Name (eg, company) [Default Company Ltd]:
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) []:mana
Email Address []:olivier.hoarau@funix.org
then the following two commands will allow us to sign the certificate with our local certification authority and give it a validity of 7300 days, enough to be at peace for a while
openssl x509 -x509toreq -in
sendmail_certreq.pem -signkey private/sendmail_key.pem -out
sendmail_csr.pem
openssl ca -policy policy_anything -days 7300 -out
sendmail_certificate.pem -infiles sendmail_csr.pem
This last command will ask for the certificate authority password
Using configuration from /etc/pki/tls/openssl.cnfEnter pass phrase for /etc/pki/CA/private/cakey.pem:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number:
11:b4:74:e2:eb:82:f6:f4:08:7d:2d:2f:81:75:e3:1e:2e:70:08:e5
Validity
Not Before: Jul 30 17:56:34 2024 GMT
Not After : Jul 25 17:56:34 2044 GMT
Subject:
countryName = Fr
stateOrProvinceName = Breizland
localityName = Brest
organizationName = Default Company Ltd
commonName = mana
emailAddress = olivier.hoarau@funix.org
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
X509v3 Subject Key Identifier:
B0:96:37:7F:5F:7E:02:E5:D2:A6:C6:9C:0E:22:4A:70:90:C7:3B:A0
X509v3 Authority Key Identifier:
5F:EF:90:A6:C4:C5:15:65:77:EE:DA:61:14:23:A4:D8:98:5D:FF:C8
Certificate is to be certified until Jul 25 17:56:34 2044 GMT (7300 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Database updated
the temporary file sendmail_csr.pem can be deleted. we give them the appropriate rights
chmod 400 /etc/pki/tls/sendmail_certificate.pem /etc/pki/tls/private/sendmail_key.pem
if you want to see what the certificate looks like you can type the command
openssl x509 -noout -text -in /etc/pki/tls/sendmail_certificate.pem
which will give something like this
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
11:b4:74:e2:eb:82:f4:f5:08:7d:2d:2f:81:75:e3:1e:2e:70:08:e6
Signature
Algorithm: sha256WithRSAEncryption
Issuer: C = FR,
ST = Bretagne, O = none, OU = none, CN = ultra.kervao.fr,
emailAddress = olivier.hoarau@funix.org
Validity
Not Before: Jul 30 20:01:57 2024 GMT
Not After: Jul 25 20:01:57 2044 GMT
Subject: C = Fr,
ST = Breizland, L = Brest, O = Default Company Ltd, CN =
ultra, emailAddress = olivier.hoarau@funix.org
Subject Public
Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:c1:37:20:73:bf:61:fa:29:0f:fa:a8:05:63:b6:
01:32:38:ee:36:30:18:13:78:65:c6:c8:52:aa:a7:
bf:82:28:aa:cb:29:ef:06:02:6b:84:44:e5:5c:1a:
(...)
we now modify the sendmail configuration file /usr/share/sendmail-cf/cf/config.mc and add at the end
define(`confCACERT_PATH',
`/etc/pki/tls/certs')dnl
define(`confCACERT',
`/etc/pki/tls/certs/ca-bundle.crt')dnl
define(`confSERVER_CERT',
`/etc/pki/tls/sendmail_certificate.pem')dnl
define(`confSERVER_KEY',
`/etc/pki/tls/private/sendmail_key.pem')dnl
- Let's recap
-
- ca-bundle.crt is the certificate of the local certification authority, its public key is embedded in the certificate
sendmail_certificate.pem is the sendmail server certificate which also includes its public key
sendmail_key.pem is the private key of the sendmail server
To rebuild the sendmail configuration file, type the command:
cd
/usr/share/sendmail-cf/cf/
m4 config.mc
> /etc/mail/sendmail.cf
we stop sendmail
systemctl stop sendmail.service
and we relaunch it
systemctl start sendmail.service
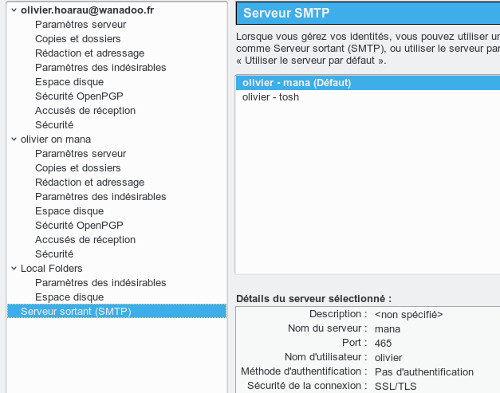
If you have a firewall on your server you will need to remember to open SMTPS port 465 and close port 25.
Now on Thunderbird we will configure the outgoing server by choosing SSL/TLS and setting port 465 like this
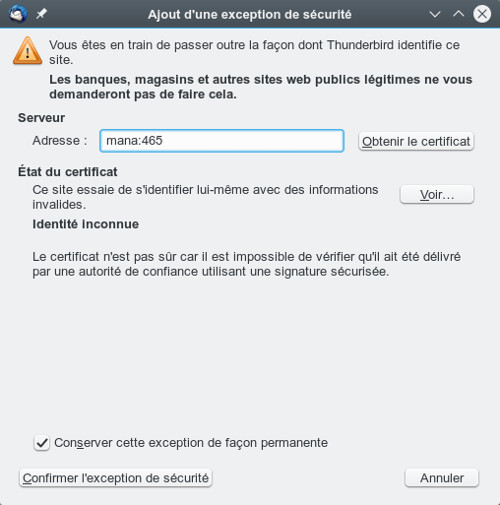
The first time you send an email you will have to accept the security exception (invalid certificate)
juil. 30 22:05:12 mana.kervao.fr sendmail[1434883]:
engine=(null), path=(null), ispre=1, pre=0, initialized=0
juil. 30 22:05:12 mana.kervao.fr sendmail[1434883]: STARTTLS:
ClientCertFile missing
juil. 30 22:05:12 mana.kervao.fr sendmail[1434883]: STARTTLS:
ClientKeyFile missing
juil. 30 22:05:12 mana.kervao.fr sendmail[1434883]: STARTTLS:
CRLFile missing
juil. 30 22:05:12 mana.kervao.fr sendmail[1434883]:
STARTTLS=client, init=1
juil. 30 22:05:12 mana.kervao.fr sendmail[1434883]:
46UK57fC1434871: SMTP outgoing connect on mana.kervao.fr
juil. 30 22:05:12 mana.kervao.fr sendmail[1434883]:
engine=(null), path=(null), ispre=0, pre=0, initialized=0
juil. 30 22:05:12 mana.kervao.fr sendmail[1434883]:
tls_clt_features=(null), relay=smtp.fai.net [51.150.205.9]
juil. 30 22:05:12 mana.kervao.fr sendmail[1434883]:
tls_clt_features=empty, stat=0, relay=smtp.fai.net
[51.150.205.9]
juil. 30 22:05:12 mana.kervao.fr sendmail[1434883]:
STARTTLS=client, start=ok
juil. 30 22:05:12 mana.kervao.fr sendmail[1434883]:
STARTTLS=client, relay=smtp.fai.net., version=TLSv1.3,
verify=OK, cipher=TLS_AES_256_GCM_SHA384, bits=
256/256
juil. 30 22:05:12 mana.kervao.fr sendmail[1434883]:
STARTTLS=client, cert-subject=/CN=*.fai.net,
cert-issuer=/C=GB/ST=Greater+20Manchester/L=Salford/O=Sectigo
+20Limited/CN=Sectigo+20RSA+20Domain+20Validation+20Secure+20Server+20CA,
verifymsg=ok
juil. 30 22:05:12 mana.kervao.fr sendmail[1434883]: AUTH=client,
relay=smtp.fai.net., mech=PLAIN, bits=0
juil. 30 22:05:12 mana.kervao.fr sendmail[1434883]:
46UK57fC1434871: to=<veronique.hoarau@funix.org>,
delay=00:00:05, xdelay=00:00:00, mailer=relay, pri=120552,
relay=smtp.fai.net. [51.150.205.9], dsn=2.0.0, stat=Sent (OK
id=1sYt5s-006KEO-Ip)
juil. 30 22:05:12 mana.kervao.fr sendmail[1434883]:
46UK57fC1434871: done; delay=00:00:05, ntries=1
juil. 30 22:05:12 mana.kervao.fr sendmail[1434883]:
STARTTLS=client, SSL_shutdown failed: -1
and with a default log level
of 9
Jul 30 22:10:13
mana.kervao.fr sendmail[1435028]: STARTTLS=client,
relay=smtp.fai.net., version=TLSv1.3, verify=OK,
cipher=TLS_AES_256_GCM_SHA384, bits=
256/256
Jul 30 22:10:13
mana.kervao.fr sendmail[1435028]: 46UKA2Fm1435016:
to=<veronique.hoarau@funix.org>, delay=00:00:10,
xdelay=00:00:00, mailer=relay, pri=120552,
relay=smtp.fai.net.
[51.150.205.9], dsn=2.0.0, stat=Sent (OK
id=1sYtAj-006Ky7-8Z)
Note that you must have verify=OK, if you have verify=FAIL it means that it does not work and it often comes from a certificate and/or key problem. To check that the server is correctly configured you can type the command below which will list the server certificates
openssl s_client -connect mana:465 -showcerts
Here is part of the result
CONNECTED(00000003)
Can't use SSL_get_servername
depth=0 C = Fr, ST = Breizland, L = Brest, O = Default Company
Ltd, CN = mana, emailAddress = olivier.hoarau@funix.org
verify error:num=20:unable to get local issuer certificate
verify return:1
depth=0 C = Fr, ST = Breizland, L = Brest, O = Default Company
Ltd, CN = mana, emailAddress = olivier.hoarau@funix.org
verify error:num=21:unable to verify the first certificate
verify return:1
depth=0 C = Fr, ST = Breizland, L = Brest, O = Default Company
Ltd, CN = mana, emailAddress = olivier.hoarau@funix.org
verify return:1
---
Certificate chain
0 s:C = Fr, ST = Breizland, L = Brest, O = Default Company
Ltd, CN = mana, emailAddress = olivier.hoarau@funix.org
i:C = FR, ST = Bretagne, O = none, OU = none, CN =
mana.kervao.fr, emailAddress = olivier.hoarau@funix.org
a:PKEY: rsaEncryption, 2048 (bit); sigalg:
RSA-SHA256
v:NotBefore: Jul 30 20:01:57 2024 GMT; NotAfter:
Jul 25 20:01:57 2044 GMT
-----BEGIN CERTIFICATE-----
MIID5jCCAs6gAwIBAgIUEbR04uuC9vUIfS0vgXXjHi5wCOYwDQYJKoZIhvcNAQEL
BQAwgYExCzAJBgNVBAYTAkZSMREwDwYDVQQIDAhCcmV0YWduZTENMAsGA1UECgwE
(...)
BM7dyjCkVYXAfOBSnFMH/oWyq2/PxW+JwxumOYnN0eYfV4LaOUXLH2E4
-----END CERTIFICATE-----
---
Server certificate
subject=C = Fr, ST = Breizland, L = Brest, O = Default Company
Ltd, CN = mana, emailAddress = olivier.hoarau@funix.org
issuer=C = FR, ST = Bretagne, O = none, OU = none, CN =
mana.kervao.fr, emailAddress = olivier.hoarau@funix.org
---
Acceptable client certificate CA names
CN = ACCVRAIZ1, OU = PKIACCV, O = ACCV, C = ES
C = ES, O = FNMT-RCM, OU = AC RAIZ FNMT-RCM
C = ES, O = FNMT-RCM, OU = Ceres, organizationIdentifier =
VATES-Q2826004J, CN = AC RAIZ FNMT-RCM SERVIDORES SEGUROS
serialNumber = G63287510, C = ES, O = ANF Autoridad de
Certificacion, OU = ANF CA Raiz, CN = ANF Secure Server Root CA
C = IT, L = Milan, O = Actalis S.p.A./03358520967, CN = Actalis
Authentication Root CA
C = US, O = AffirmTrust, CN = AffirmTrust Commercial
C = US, O = AffirmTrust, CN = AffirmTrust Networking
etc.
in thunderbird in the preferences, we can view the certificate (we can also see that of dovecot )
To tell the truth, you just have to test it. We will send an email then force a sending with sendmail in verbose mode like this
sendmail -q -vhere is the response from the ISP's SMTP server
<veronique.hoarau@funix.org>...
Connecting to smtp.fai.net. via relay...
220 smtp.fai.net ESMTP
Exim 4.93 Ubuntu Wed, 31 Jul 2024 13:52:12 +0200
>>> EHLO fai.net
the local server sends him a hello
>>> EHLO fai.net
the ISP server sends it its features
250-smtp.fai.net Hello
fai.net [XXX.XXX.XXX.XXX]
250-SIZE 52428800
250-8BITMIME
250-PIPELINING
250-AUTH PLAIN LOGIN
250-CHUNKING
250-STARTTLS
250-SMTPUTF8
250 HELP
The PIPELINING command allows you to speed up the SMTP connection by sending the commands in one block and not one after the other.
SIZE 52428800 indicates that emails are limited to 52MB
8BITMIME transfer mode under 8 bits to pass all UTF-8 characters
AUTH PLAIN LOGIN is the authentication method which is in this case PLAIN, which does not mean that the exchange of login and password is done in clear text, but it is encrypted in base64
and finally STARTTLS to switch to encrypted mode with TLSmy server therefore launches an encrypted connection
>>> STARTTLS
here is the response from the ISP's SMTP server
220 TLS go
ahead
>>> EHLO fai.net and the numericable SMTP
server sends its functionalities again
250-smtp.fai.net
Hello fai.net [XXX.XXX.XXX.XXX]
250-SIZE 52428800
250-8BITMIME
250-PIPELINING
250-AUTH PLAIN LOGIN
250-CHUNKING
250-SMTPUTF8
250 HELP
the mail transfer is then carried out with a dialogue between the 2 servers
>>> AUTH PLAIN
b2xpdmllci5ob2FyYXVAZnVuaXgub3JnAG9saXZpZXIuaG9hcmF1QGZ1bml4Lm9yZwBUb2hlX3RvbmUyOT8=
235 Authentication
succeeded
>>> MAIL
From:<olivier.hoarau@funix.org> SIZE=1026 BODY=7BIT
250 OK
>>> RCPT
To:<veronique.hoarau@funix.org>
>>> DATA
250 Accepted
354 Enter message, ending
with "." on a line by itself
>>> .
250 OK id=1sZ7sL-008oFp-1W
<veronique.hoarau@funix.org>... Sent (OK
id=1sZ7sL-008oFp-1W)
Closing connection to
smtp.fai.net.
>>> QUIT
221 smtp.fai.net closing
connection
Also note that in the header of the email that was sent, we see that the transmission was indeed encrypted.
Received: from
[XXX.XXX.XXX.XXX] (helo=fai.net)
by smtp.fai.net
with esmtpsa (TLS1.3) tls
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
(Exim 4.93)
(envelope-from
<olivier.hoarau@funix.org>)
id
1sYsl5-006Gpa-66
for
veronique.hoarau@funix.org; Tue, 30 Jul 2024 21:43:43 +0200
Sendmail and the fight against spam
FEATURE(dnsbl, `blackholes.mail-abuse.org', `Rejected - see http://www.mail-abuse.org/rbl/')dnl
FEATURE(dnsbl, `dialups.mail-abuse.org', `Dialup - seehttp://www.mail-abuse.org/dul/')dnl
FEATURE(dnsbl, `relays.mail-abuse.org', `Open spam relay - seehttp://www.mail-abuse.org/rss/')dnl
FEATURE(`dnsbl', `list.dsbl.org')dnl
FEATURE(`dnsbl', `bl.spamcop.net')dnl
FEATURE(`dnsbl', `sbl.spamhaus.org')dnl
You must then rebuild /etc/mail/sendmail.cf with m4 and restart sendmail.
Secure Sendmail
The vrfy and expn commands
telnet mana 25
here is the result
Trying 192.168.13.11...
Connected to
mana.kervao.fr (192.168.2.13).
Escape character is '^]'.
220 fai.net ESMTP Sendmail
8.17.1/8.17.1/Sendmail from FUNIX; Wed, 31 Jul 2024 14:27:41
+0200
You have vrfy (verify) to check the existence of an address on the server
vrfy olivier
250 2.1.5
olivier@rennes-1-a7-7-251.dial.proxad.net
When the user is unknown
vrfy toto
550 5.1.1 toto... User
unknown
You have the expn (expand) command which is identical to vrfy but also allows you to list people on a list and other aliases.
expn olivier
250 2.1.5
olivier@rennes-1-a7-7-251.dial.proxad.net
To disable the vfry and expn commands you must add the following line to the config.mc configuration file :
define(`confPRIVACY_FLAGS', `novrfy noexpn')dnl
Here is the result:
vrfy olivier
252 2.5.2 Cannot VRFY user;
try RCPT to attempt delivery (or try finger)
NOTE To exit telnet, simply type quit
Change sendmail prompt
By doing a telnet we can obtain information on the sendmail server, to avoid this, we can add the following line in the config.mc configuration file :define(`confSMTP_LOGIN_MSG',`Mail server; $b')dnl
This is what it looks like:
telnet zoulou 25
Trying 192.168.13.11...
Connected to
zoulou.kervao.fr.
Escape character is '^]'.
220 ESMTP mail server; Sun,
17 Jun 2001 09:19:37 -0400
Some explanations
The points below are for informational purposes for the curious to explain some sendmail configuration options .Domain masking
If you send an email to echo addresses like echo@univie.ac.at, it will simply send you your email with the full header of the original email, and you may see indiscreet information that you might not want to see.Here is the email that leaves the Linux server, with the following content:
Subject:
first line test
Content of the response email from the echo server:
--------------------------------------------------------
Vienna University Computer Center - Echo Service
echo@univie.ac.at
This message was generated upon your request by the
automatic
answering service.
Answers are limited to _one_every_two_minutes_ to
prevent
abuse!
Attached you'll find the first 4 kByte of your mail.
--------------------------------------------------------
> From toto.nom@fai.fr Tue Aug 10 22:25:27 1999
> Received: from obelix.fai.fr (obelix.fai.fr
[210.205.98.21])
> by
fermi.cnam.fr (8.8.8/jpm-301097) with ESMTP id WAA11452
> for
<echo@cnam.fr>; Tue, 10 Aug 1999 22:25:27 +0200 (MET DST)
> From: toto.nom@fai.fr
> Return-Path: <toto.nom@fai.fr>
> Received: from machine.domaine.fr
(IDENT:root@ppptc22.fai.fr [210.205.98.22])
> by obelix.fai.fr
(8.9.1/8.9.1/R&D&B-990119) with ESMTP id WAA26056
> for
<echo@cnam.fr>; Tue, 10 Aug 1999 22:24:55 +0200
> Received: (from toto@localhost)
> by machine.domaine.fr
(8.9.3/8.9.3/Commentaire quelconque) id WAA00754
> for echo@cnam.fr; Tue,
10 Aug 1999 22:25:34 +0200
> Date: Tue, 10 Aug 1999 22:25:34 +0200
> Message-Id:
<199908102025.WAA00754@machine.domaine.fr>
> To: echo@cnam.fr
> Subject: test
------
>
> première ligne
>
------ Fin de votre message
Some comments:
toto.nom@fai.fr is your email address at your access provider, obelix.fai.fr (IP= 210.205.98.21) is the name of the machine at
your ISP that "routed" your
email, ppptc22.fai.fr (IP=210.205.98.22) is your official identity on the
net at the time of your connection. You see that the name of
your domain appears in the Received
fields , and even the
comment that you will have defined in the sendmail configuration file . Some email managers could
reject your emails under the pretext of containing an unknown
domain name.
Now let's look at an email
arriving from one of your Windows workstations and going out
onto the net.
> From toto.nom@fai.fr
Tue Aug 10 19:47:07 1999
> Received: from
obelix.fai.fr (obelix.fai.fr [210.205.98.21])
> by fermi.cnam.fr
(8.8.8/jpm-301097) with ESMTP id TAA05598
> for
<echo@cnam.fr>; Tue, 10 Aug 1999 19:47:06 +0200 (MET
DST)
> Return-Path:
<toto.nom@fai.fr>
> Received: from
machine.domaine.fr (IDENT:root@ppptc32.fai.fr
[210.205.98.23])
> by obelix.fai.fr
(8.9.1/8.9.1/R&D&B-990119) with ESMTP id TAA23230
> for
<echo@cnam.fr>; Tue, 10 Aug 1999 19:46:35 +0200
> Received: from windows
(windows.domaine.fr [192.168.13.11])
> by machine.domaine.fr
(8.9.3/8.9.3/Any comment) with ESMTP id TAA00863
> for
<echo@cnam.fr>; Tue, 10 Aug 1999 19:38:54 +0200
> Message-Id:
<199908101738.TAA00863@machine.domaine.fr>
> From: "Toto Nom"
<toto.nom@fai.fr>
> To:
<echo@cnam.fr>
> Subject: windows test
> Date: Tue, 10 Aug 1999
19:37:08 +0200
> X-MSMail-Priority:
Normal
> X-Priority: 3
> X-Mailer: Microsoft
Internet Mail 4.70.1155
> MIME-Version: 1.0
> Content-Type:
text/plain; charset=UTF-8
>
Content-Transfer-Encoding: 7bit
------
>
> first line
>
------ End of your message
In Received , we actually see the path followed by the email sent from the Windows workstation , goes to the machine then to your ISP (on Obelix ), we therefore see the name of your domain, the names of the Linux workstation and the workstation on your private network from which the email was sent, and even the IP address that you assigned to it!
The problem is that we cannot remove the Received fields in the sendmail config parameters, FEATURE(masquerade_enveloppe) only masks the email addresses.
To fix this, we will first
add define(`confDOMAIN_NAME',`ppp.fai.fr') which allows us to redefine the way our Linux
server will present itself to the provider's SMTP server, in
short it will change all occurrences of machine.domain.fr to ppp.fai.fr in
the Received fields . Why put ppp.fai.fr and not just put fai.fr, because in this case we will not be able to send
mail to users of the fai.fr domain, sendmail thinks they are local users! With ppp.fai.fr no problem, strictly speaking we could put here the
name assigned during a connection (like ppp18-brest.fai.fr which we can see by typing ifconfig ).
The problem remains of
emails from Windows workstations, where the name and IP
address appear, we will completely redefine the Received field :
define(`confRECEIVED_HEADER',
`from fai.fr
by fai.fr ($v/$Z)$?r with $r$. id $i$?u
for $u; $|;
$.$b')
Which gives us for an email sent from a PC under Windows:
> From
toto.nom@fai.fr@funix.org Sat Jun 01 17:08:31 2002
> Return-Path:
<toto.nom@fai.fr>
> Delivered-To:
echo@cnam.fr
> Received: (qmail 20719
invoked from network); 1 Jun 2002 17:08:31 -0000
> Received: from
bougainville.cnam.fr (163.173.128.13)
> by 0 with SMTP; 1 Jun
2002 17:08:31 -0000
> Received: from
localhost (localhost [127.0.0.1])
> by
bougainville.cnam.fr (Postfix) with ESMTP id 132F82EFB4
> for
<echo@cnam.fr>; Sat, 1 Jun 2002 19:08:31 +0200 (CEST)
> Received: from
smtp.fai.fr (mail.fai.fr [202.3.225.22])
> by
bougainville.cnam.fr (Postfix) with ESMTP id D31492EFAE
> for
<echo@cnam.fr>; Sat, 1 Jun 2002 19:08:27 +0200 (CEST)
> Received: from
ppp.fai.fr (tc5-bis-014.dialup.fai.fr [202.3.239.14])
> by smtp.fai.fr
(Mirapoint Messaging Server MOS 3.1.0.36-EA)
> with ESMTP id ADS19083
> for
<echo@cnam.fr>;
> Sat, 1 Jun 2002
07:08:20 -1000 (TAHT)
> Received: from fai.fr
> by fai.fr
(8.12.1/8.12.1/Any comment) with ESMTP id g51H7FAj002161
> for
<echo@cnam.fr>; Sat, 1 Jun 2002 07:07:15 -1000
> Message-ID:
<3CF90D0A.5FF74480@fai.fr>
> Date: Sat, 01 Jun 2002
07:06:02 -1100
> From: Toto Nom
<toto.nom@fai.fr>
> X-Mailer: Mozilla 4.7
[fr] (WinNT; I)
> X-Accept-Language: fr
> MIME-Version: 1.0
> To: echo@cnam.fr
> Subject: essay
> Content-Type:
text/plain; charset=us-ascii
>
Content-Transfer-Encoding: 7bit
> X-Virus-Scanned: by
AMaViS perl-11
------
>
> first line
>
------ End of your message
Here is the email that comes from our Linux server.
> From toto.nom@fai.fr
Sat Jun 01 05:51:15 2002
> Return-Path:
<toto.nom@fai.fr>
> Delivered-To:
echo@cnam.fr
> Received: (qmail 3855
invoked from network); 1 Jun 2002 05:51:14 -0000
> Received: from
bougainville.cnam.fr (163.173.128.13)
> by 0 with SMTP; 1 Jun
2002 05:51:14 -0000
> Received: from
localhost (localhost [127.0.0.1])
> by
bougainville.cnam.fr (Postfix) with ESMTP id CB0A52EFAF
> for
<echo@cnam.fr>; Sat, 1 Jun 2002 07:51:14 +0200 (CEST)
> Received: from
smtp.fai.fr (mail.fai.fr [202.3.225.22])
> by
bougainville.cnam.fr (Postfix) with ESMTP id 8EE6D2EFAE
> for
<echo@cnam.fr>; Sat, 1 Jun 2002 07:51:11 +0200 (CEST)
> Received: from
ppp.fai.fr (tc5-bis-198.dialup.fai.fr [202.3.239.198])
> by smtp.fai.fr
(Mirapoint Messaging Server MOS 3.1.0.36-EA)
> with ESMTP id ADS03894
> for
<echo@cnam.fr>;
> Fri, 31 May 2002
19:50:40 -1000 (TAHT)
> Received: from fai.fr
> by fai.fr
(8.12.1/8.12.1/Any comment) with ESMTP id g515nwFE002664
> for
<echo@cnam.fr>; Fri, 31 May 2002 19:49:58 -1000
> Sender:
toto.nom@fai.fr
> Message-ID:
<3CF86086.351F9560@fai.fr>
> Date: Fri, 31 May 2002
19:49:58 -1000
> From: Toto Nom
<toto.nom@fai.fr>
> Organization: Tahiti
Connection > X - Mailer: Mozilla 4.78 [ fr ]
(X11; U; Linux 2.4.18-6mdk
i686 )
> charset=us-ascii >
Content-Transfer-Encoding: 7bit > X-Virus-Scanned: by
AMaViS perl-11 ---
---
>
> first line
>
------ End of your message
If you have an email other than the one assigned by the ISP used
You can very well use an ISP like fai.fr and not use an email address in @fai.fr . So I connect with free and my email address is olivier.hoarau@fnac.net, in this case the Message-Id and the Sender do not look good.Example with this header returned by the echo service.
> From
olivier.hoarau@fnac.net Sat Jul 15 08:19:16 2000
> Received: from
postfix3.free.fr (postfix@postfix3.free.fr [212.27.32.22])
> by fermi.cnam.fr
(8.8.8/jpm-301097) with ESMTP id IAA05796
> for
<echo@cnam.fr>; Sat, 15 Jul 2000 08:19:16 +0200 (MET
DST)
> Return-Path:
<olivier.hoarau@fnac.net>
> Received: from
ppp.free.fr (massy-4-14-209.dial.proxad.net
[213.228.14.209])
> by postfix3.free.fr
(Postfix) with ESMTP id 62B6286B67
> for
<echo@cnam.fr>; Sat, 15 Jul 2000 08:19:15 +0200 (CEST)
> Received: from free.fr
> by free.fr
(8.10.1/8.10.1/Olivier Hoarau-992911) with ESMTP id
e6F68IJ01419
> for
<echo@cnam.fr>; Sat, 15 Jul 2000 08:08:18 +0200
> Sender:
olivier@free.fr
> Message-ID:
<396FFFD2.447D80E1@fnac.net>
> Date: Sat, 15 Jul 2000
08:08:18 +0200
> From: Olivier Hoarau
<olivier.hoarau@fnac.net>
> Organization: Breizh
Connection > X- Mailer : Mozilla 4.73 [fr ]
(X11; I; Linux 2.2.15-4mdk
i686 )
> charset=us-ascii
>
Content-Transfer-Encoding: 7bit
You see that the Message-Id has the extension fnac.net whereas it should be in free.fr since I use free, likewise the
Sender is olivier@free.fr which does not correspond to anything, since my
email at free is ohoarau@free.fr
To solve the problem of the
Message-Id and the Sender, I wrote this little script:
#!/bin/bash
cd /var/spool/mqueue
for mail_name in $(ls qf*)
do
awk 'BEGIN { FS=":" }
$1!="H??Message-ID" && $1!= "H??Sender" { print $0 }
$1=="H??Sender" { sub("olivier","ohoarau",$2);print
$1,":",$2 }
$1=="H??Message-ID" { sub("fnac.net","free.fr",$2); print
$1,":",$2 }
' $mail_name > /tmp/mail.tmp
cp /tmp/mail.tmp $mail_name
done
You can easily adapt this
script to your situation, some comments may be useful:
- sub("olivier","ohoarau",$2) here it is to have Sender: ohoarau@free.fr instead of Sender: olivier@free.fr
-
sub("fnac.net","free.fr",$2) here it is to have Message-ID: <396FFFD2.447D80E1@free.fr instead of Message-ID: <396FFFD2.447D80E1@fnac.net
Replace the appropriate
strings to make it work for you. The script owner must be
root, with 755 rights, it will be called before sendmail -q and will allow you to change the Message-Id and the Sender.
If this script is called chg-message and is located in /usr/sbin, you must launch it before each mail sent by sendmail, it is possibly configurable via cron .
/usr/sbin/chg-message
/usr/sbin/sendmail -q
Here is the final header of my email sent from my Linux workstation as returned by the CNAM echo server:
> From
olivier.hoarau@fnac.net Sat Jul 15 09:23:09 2000
> Received: from
postfix1.free.fr (postfix@postfix1.free.fr [212.27.32.21])
> by fermi.cnam.fr
(8.8.8/jpm-301097) with ESMTP id JAA10064
> for
<echo@cnam.fr>; Sat, 15 Jul 2000 09:23:09 +0200 (MET
DST)
> Return-Path:
<olivier.hoarau@fnac.net>
> Received: from
ppp.free.fr (massy-2-11-231.dial.proxad.net
[213.228.11.231])
> by postfix1.free.fr
(Postfix) with ESMTP id DA7D228043
> for
<echo@cnam.fr>; Sat, 15 Jul 2000 09:23:03 +0200 (MEST)
> Received: from free.fr
> by free.fr
(8.10.1/8.10.1/Olivier Hoarau-992911) with ESMTP id
e6F72bP02146
> for
<echo@cnam.fr>; Sat, 15 Jul 2000 09:02:37 +0200
> Sender:
ohoarau@free.fr
> Message-ID:
<39700C8D.3443567C@free.fr>
> Date: Sat, 15 Jul 2000
09:02:37 +0200
> From: Olivier Hoarau
<olivier.hoarau@fnac.net>
> Organization: Breizh
Connection > X- Mailer : Mozilla 4.73 [fr ]
(X11; I; Linux 2.2.15-4mdk
i686 )
> charset=us-ascii
>
Content-Transfer-Encoding: 7bit
The Message-Id and Sender now look good.
Here is the message returned from an email from a Windows client workstation on the network:
> From
olivier.hoarau@fnac.net Sat Jul 15 09:46:21 2000
> Received: from
postfix2.free.fr (postfix@postfix2.free.fr [212.27.32.74])
> by fermi.cnam.fr
(8.8.8/jpm-301097) with ESMTP id JAA11374
> for
<echo@cnam.fr>; Sat, 15 Jul 2000 09:46:21 +0200 (MET
DST)
> Return-Path:
<olivier.hoarau@fnac.net>
> Received: from
ppp.free.fr (massy-2-10-239.dial.proxad.net
[213.228.10.239])
> by postfix2.free.fr
(Postfix) with ESMTP id 7FB1D740DB
> for
<echo@cnam.fr>; Sat, 15 Jul 2000 09:46:20 +0200 (MEST)
> Received: from free.fr
> by free.fr
(8.10.1/8.10.1/Olivier Hoarau-992911) with ESMTP id
e6F7iTG02453
> for
<echo@cnam.fr>; Sat, 15 Jul 2000 09:44:30 +0200
> Message-ID:
<39701660.10A22F73@free.fr>
> Date: Sat, 15 Jul 2000
09:44:32 +0200
> From: Olivier Hoarau
<olivier.hoarau@fnac.net>
> X-Mailer: Mozilla 4.6
[fr] (Win98; I)
> X-Accept-Language: fr
> MIME-Version: 1.0
> To: echo@cnam.fr
> Subject: tavel
> Content-Type:
text/plain; charset=us-ascii
>
Content-Transfer-Encoding: 7bit
------
You can see that there is no Sender field .
| [ Back to FUNIX home page ] |
 Welcome
Welcome Linux
Linux Unix
Unix Download
Download