Last modified August 4, 2022
User Authentication with LDAP
Network and system
This site has been automatically translated with Google Translate from this original page written in french, there may be some translation errors
Presentation
In the following operations, we will call the server the machine which centralizes the definition of all users and groups; the client calls the server for user authentication.
Facility
We will retrieve from this site https://src.fedoraproject.org/repo/pkgs/openldap/MigrationTools-47.tar.gz the tarball MigrationTools-4.7.tar.gz we uncompress it by typingtar xvfz MigrationTools-4.7.tar.gz
This gives the MigrationTools-47 directory
Now we will install nss-pam-ldapd which provides a Name Service Switch ( NSS ) module that accesses account information and any other information found in system files ( hosts , aliases , netgroups , etc...). It also provides a PAM (Pluggable Authentication Module) module for an LDAP server.
systemctl enable nslcd.service
here is the result
Created symlink from /etc/systemd/system/multi-user.target.wants/nslcd.service to /usr/lib/systemd/system/nslcd.service.
we will try to launch it after configuring the /etc/nslcd.conf file (see below )
Configuration
Configuring a server
The slapd server is configured as described in its dedicated page.Now in the MigrationTools-47 directory , we will modify the migrate_common.ph file, we must indicate its domain name, like this:
# Default DNS domain
$DEFAULT_MAIL_DOMAIN =
"kervao.fr";
# Default base
$DEFAULT_BASE =
"dc=kervao,dc=fr";
Optionally you can modify
the following line specifying the mail server although it is
not absolutely necessary.
$DEFAULT_MAIL_HOST = "mail.padl.com";
Now we need to enter the system users and groups into the LDAP database. Let's start by creating temporary files in ldif format. Now we type as root (to be able to read /etc/shadow )
ETC_SHADOW=/etc/shadow
export
ETC_SHADOW
./migrate_passwd.pl
/etc/passwd /tmp/passwd.ldif
./migrate_group.pl
/etc/group /tmp/group.ldif
Edit both ldif files to leave only users, remove all system users and groups (root, lp, sys, apache, ...). Here is the content of my group.ldif with my user group hoarau
dn:
cn=hoarau,ou=Group,dc=kervao,dc=fr
objectClass: posixGroup
objectClass: top
cn: hoarau
userPassword: {crypt}*
gidNumber: 5000
memberUid: olivier
memberUid: veronique
Here now is the content of my passwd.ldif with my two users
dn:
uid=olivier,ou=People,dc=kervao,dc=fr
uid: olivier
cn: olivier
objectClass: account
objectClass:
posixAccount objectClass:
top
objectClass: shadowAccount
userPassword:
{crypt}$1$76UeLH8Z$K8rdYPRmUoiONZQm6hV4q.
shadowLastChange: 11858
shadowMax: 99999
shadowWarning: 7
shadowInactive: -1
shadowExpire: -1
shadowFlag: 1081428222
loginShell: /bin/bash
uidNumber: 5001
gidNumber: 5000
homeDirectory:
/home/olivier
gecos: olivier
dn:
uid=veronique,ou=People,dc=kervao,dc=fr
uid: veronique
cn: veronique
objectClass: account
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword:
{crypt}$1$OyedUoIU$uwpYR0bWJGzF4AFAHspSm/
shadowLastChange: 11858
shadowMax: 99999
shadowWarning: 7
shadowInactive: -1
shadowExpire: -1
shadowFlag: 1081428222
loginShell: /bin/bash
uidNumber: 5002
gidNumber: 5000
homeDirectory:
/home/veronique
gecos: veronique
Now we will need to create the temp.ldif file which will contain the definition of the Organizational Unit ( ou ) Group (user group) and People (user). Here is its content:
dn: dc=kervao,dc=fr
objectClass: dcObject
objectClass: organization
dc: kervao
o: kervao.fr
dn:
ou=Group,dc=kervao,dc=fr
ou: Group
objectClass: top
objectClass:
organizationalUnit
description: user group
dn:
ou=People,dc=kervao,dc=fr
ou: People
objectClass: top
objectClass:
organizationalUnit
description: system users
We can start adding all this (in verbose mode), in the base, we start with the ou Group and People
ldapadd -v -x -D "cn=Manager,dc=kervao,dc=fr" -W -f /tmp/temp.ldif
here is the result
ldap_initialize(
<DEFAULT> )
Enter LDAP Password:
add objectClass:
dcObject
organization
add dc:
kervao
add o:
kervao.fr
adding new entry
"dc=kervao,dc=fr"
modify complete
add ou:
Group
add objectClass:
top
organizationalUnit
add description:
group of users
adding new entry
"ou=Group,dc=kervao,dc=fr"
modify complete
add ou:
People
add objectClass:
top
organizationalUnit
add description:
system users
adding new entry
"ou=People,dc=kervao,dc=fr"
modify complete
ldapadd -x -D
"cn=Manager,dc=kervao,dc=fr" -f /tmp/passwd.ldif -W
Enter LDAP Password:
adding new entry
"uid=olivier,ou=People,dc=kervao,dc=fr"
adding new entry "uid=veronique,ou=People,dc=kervao,dc=fr"
Then
ldapadd -x -D
"cn=Manager,dc=kervao,dc=fr" -f /tmp/group.ldif -W
Enter LDAP Password:
adding new entry
"cn=hoarau,ou=Group,dc=kervao,dc=fr"
We visualize all this by typing
ldapsearch -x -D
"cn=Manager, dc=kervao, dc=fr" -W -b "dc=kervao,dc=fr"
Enter LDAP Password:
version: 2
#
# filter: (objectclass=*)
# requesting: ALL
#
# kervao, fr
dn: dc=kervao, dc=fr
objectClass: dcObject
objectClass: organization
dc: kervao.fr
o: kervao.fr
# Group, kervao, fr
dn:
ou=Group,dc=kervao,dc=fr
ou: Group
objectClass: top
objectClass:
organizationalUnit
description: user group
# People, kervao, fr
dn:
ou=People,dc=kervao,dc=fr
ou: People
objectClass: top
objectClass:
organizationalUnit
description: system users
# hoarau, Group, kervao, fr
dn:
cn=hoarau,ou=Group,dc=kervao,dc=fr
objectClass: posixGroup
objectClass: top
cn: hoarau
gidNumber: 5000
memberUid: olivier
memberUid: veronique
# olivier, People, kervao,
fr
dn:
uid=olivier,ou=People,dc=kervao,dc=fr
uid: olivier
cn: olivier
objectClass: account
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword::
e2NyeXB0fSQxJDc2VWvMSDhaJEs4cmRVUFJtVW5pT05aUW02aFY0cS4=
shadowLastChange: 11858
shadowMax: 99999
shadowWarning: 7
shadowInactive: -1
shadowExpire: -1
shadowFlag: 1081428222
loginShell: /bin/bash
uidNumber: 5001
gidNumber: 5000
homeDirectory:
/home/olivier
gecos: olivier
# veronique, People,
kervao, fr
dn:
uid=veronique,ou=People,dc=kervao,dc=fr
uid: veronique
cn: veronique
objectClass: account
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword::
e2NyeXB0fSQxJE95aWRVb0lVJHV3cFlOM7JXSkd6RjRBRkFIc3BTbS8=
shadowLastChange: 11858
shadowMax: 99999
shadowWarning: 7
shadowInactive: -1
shadowExpire: -1
shadowFlag: 1081428222
loginShell: /bin/bash
uidNumber: 5002
gidNumber: 5000
homeDirectory:
/home/veronique
gecos: veronique
# search result
search: 2
result: 0 Success
# numResponses: 7
# numEntries: 6
Server and Client Configuration
For a client under mageia you must install the following packagesopenldap
nss-pam-ldapd
The client relies on nslcd (Name Service LDAP Connection Daemon), note that on a server if you also want to connect to the LDAP daemon, you will have to configure it as a client. We edit the file /etc/nslcd.conf and make the following changes
# The user and group nslcd should run as.uid nslcd , this has no impact on the operation
gid nslcd
# the LDAP server
uri ldap://192.168.13.11/
# The distinguished name of the search base which must be identical to the slapd
base configuration dc=kervao, dc=fr # The distinguished name to bind to the server with which must be identical to
the slapd configuration
binddn cn=Manager,dc=kervao,dc=fr
# The credentials to bind with, be careful we must put here in clear the password that is defined in the slapd.conf file of the server
bindpw slapd-password-enclair
# Customize certain database
lookups.
base group
ou=Group,dc=kervao,dc=fr
base passwd
ou=People,dc=kervao,dc=fr
base shadow
ou=People,dc=kervao,dc=fr
map shadow userPassword userPassword
As the password is in clear text, you will need to ensure that the file rights are set to 600
-rw------- 1 root root 4855 Jul 17 08:04 /etc/nslcd.conf
In the /etc/nsswitch.conf file we will modify the following lines to read
passwd: files nis ldap
shadow: files
nis ldap
group: files nis ldap
Note that nis is not necessary if you have not set up a NIS domain.
So let's take our system-auth file again, it should look like this (add only the lines concerning pam_ldap and leave the others):
auth required pam_env.soauth sufficient pam_tcb.so shadow nullok prefix=$2a$ count=8
auth required pam_deny.so
auth sufficient pam_ldap.so
account sufficient pam_tcb.so shadow
account required pam_deny.so
account sufficient pam_ldap.so
password required pam_cracklib.so try_first_pass retry=3 minlen=4 dcredit=0 ucredit=0
password sufficient pam_tcb.so use_authtok shadow write_to=shadow nullok prefix=$2a$ count=8
password required pam_deny.so
password sufficient pam_ldap.so
session optional pam_keyinit.so revoke
session required pam_limits.so
session [success=1 default=ignore] pam_succeed_if.so service in crond quiet use_uid
-session optional pam_systemd.so
session required pam_tcb.so
session sufficient pam_ldap.so
Restart LDAP on the client (or server) now
systemctl restart nslcd
or launch it if it wasn't originally
systemctl start nslcd
Note that the /etc/ldap.conf file is no longer useful, you can ignore it superbly.
to know the status of the daemon we will type
systemctl status nslcd.service
here is the result
●
nslcd.service - Naming services LDAP client daemon
Loaded: loaded (/usr/lib/systemd/system/nslcd.service;
enabled; vendor preset: disabled)
Active: active (running) since Sun 2022-07-17 09:04:50 CEST;
5s ago
Process: 84574 ExecStart=/usr/sbin/nslcd (code=exited,
status=0/SUCCESS)
Main PID:
84576 (nslcd)
Tasks: 6 (limit: 2289)
Memory: 1.0M
CPU: 9ms
CGroup: /system.slice/nslcd.service
└─84576 /usr/sbin/nslcd
Jul 17 09:04:50
tahiti.kervao.fr systemd[1]: Starting Naming services LDAP
client daemon...
Jul 17 09:04:50
tahiti.kervao.fr nslcd[84576]: version 0.9.11 starting
Jul 17 09:04:50
tahiti.kervao.fr nslcd[84576]: DEBUG:
initgroups("nslcd",977) done
Jul 17 09:04:50
tahiti.kervao.fr nslcd[84576]: DEBUG: setgid(977) done
Jul 17 09:04:50
tahiti.kervao.fr nslcd[84576]: DEBUG: setuid(983) done
Jul 17 09:04:50
tahiti.kervao.fr nslcd[84576]: DEBUG: unlink() of
/var/run/nslcd/socket failed (ignored): No such file or
directory Jul
17 09:04:50
tahiti.kervao.fr nslcd[84576]: accepting connections
Jul 17 09:04:50
tahiti.kervao.fr systemd[1]: Started Naming services LDAP
client daemon.
If the LDAP server is configured for encrypted connection , the /etc/nslcd.conf file will be modified.
# we must indicate here ldaps which is the LDAP protocol over SSL, I had to indicate the name of my slapd server because its certificate references it by its name and not by its IP address
uri
ldaps://serveur-slapd.kervao.fr/
# Use
StartTLS without verifying the server certificate.
#ssl start_tls
#tls_reqcert allow
# CA certificates for
server certificate verification, here we indicate the path
of the slapd server certificate that must be placed in the
/etc/openldap/cacerts directory of the client
tls_cacertdir
/etc/openldap/cacerts
tls_cacertfile
/etc/openldap/cacerts/ldapcrt.pem
we stop nslcd , if we restart it in debug mode, this is what we can see (extract)
Jul 17
09:01:17 tahiti.kervao.fr nslcd[84462]: [43a858]
<passwd=5008> DEBUG:
ldap_initialize(ldaps://serveur-slapd.kervao.fr/)
Function test
It's simple whether on the server or the client, delete the lines that correspond to your users in /etc/passwd, and /etc/shadow and do the same for your user groups in /etc/group. Don't forget to make a backup of these files just in case! Now try to log in as a simple user, and there normally, you should log in without problem.Use
Create a new user
Now to create a new user, useradd does not work, because it relies only on /etc/passwd . We must first define a password. We use the slappasswd function for this.slappasswd -v -s toto345 -h {CRYPT}
We obtain
{CRYPT}rURm18fYhMvew
You will need to
create a new.ldif file that will look like this:
dn:
uid=user,ou=People,dc=kervao,dc=fr
uid: user
cn: user
objectClass: account
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword:
{CRYPT}rURm18fYhMvew
shadowLastChange: 11858
shadowMax: 99999
shadowWarning: 7
shadowInactive: -1
shadowExpire: -1
shadowFlag: 1081428222
loginShell: /bin/bash
uidNumber: 5004
gidNumber: 5000
homeDirectory: /home/user
gecos: user
For the record, here is the meaning of each of the shadow password parameters
shadowLastChange: last modification date (in days since 1.1.70),
shadowMax : maximum number of days of password usage (change
required after), no validity period if equal to 99999
shadowWarning: number of days before expiration to warn the user,
shadowInactive : number of days after the expiration date where
the account is made inactive, functionality disabled if equal
to -1
shadowExpire : number of days after 1.1.70 where the account
will be deactivated, functionality disabled if equal to -1
shadowFlag: useless (available for future use).
ATTENTION There must be no spaces or tabs at the end of the lines in your ldif file
We type ldapadd for user input into the database
ldapadd -x -D
"cn=Manager,dc=kervao,dc=fr" -f /tmp/new.ldif -W
Enter LDAP Password:
adding new entry
"uid=user,ou=People,dc=kervao,dc=fr"
That's not all, we must now indicate that this user belongs to the hoarau group. We create this file groupe.ldif containing
dn:
cn=hoarau,ou=Group,dc=kervao,dc=fr
Add: memberUid
memberUid: user
We modify the base by typing
ldapmodify -x -D
"cn=Manager, dc=kervao, dc=fr" -W -f groupe.ldif
Enter LDAP Password:
modifying entry
"cn=hoarau,ou=Group,dc=kervao,dc=fr"
However, you will have to manually create the home directory as root by typing:
mkdir /home/user
cp -R /etc/skel/*
/home/user
chown -R user:hoarau
/home/user
Add a group
Without going into the details of the commands, the ldif file to create for entering a new group is as followsdn:
cn=newgroupe,ou=Group,dc=kervao,dc=fr
objectClass: posixGroup
objectClass: top
cn: newgroupe
gidNumber: 5000
Here is the file to add users to the group
dn:
cn=newgroupe,ou=Group,dc=kervao,dc=fr
Add: memberUid
memberUid: new-user
Delete a user
To delete the user user we will typeldapdelete -x -D
"cn=Manager, dc=kervao, dc=fr"
"uid=user,ou=People,dc=kervao,dc=fr" -W
We will then create a delete.ldif file containing
dn:
cn=hoarau,ou=Group,dc=kervao,dc=fr
delete: memberUid
memberUid: user
We are typing now
ldapmodify -x -D
"cn=Manager, dc=kervao, dc=fr" -W -f delete.ldif
Enter LDAP Password:
modifying entry
"cn=hoarau,ou=Group,dc=kervao,dc=fr"
Change your password
Now the problem is to change the password without having to go through the Manager. A simple user must be able to change his own password, let's take the case of the user olivier, he must first find one with the slappasswd commandslappasswd -v -s tutu728 -h {CRYPT}
This is the result
{CRYPT}WW6h470hoW4nI
It now creates the file modif.ldif containing
dn: uid=olivier, ou=People,
dc=kervao, dc=fr
changetype: modify
replace: userPassword
userPassword:
{CRYPT}WW6h470hoW4nI
And he modifies the base by typing
[olivier@asterix olivier]$
ldapmodify -x -D "uid=olivier, ou=People, dc=kervao, dc=fr"
-f /tmp/modif.ldif -W
Enter LDAP Password: (olivier password)
modifying entry
"uid=olivier, ou=People, dc=kervao, dc=fr"
Here is his password changed. You will tell me it is very complicated, there is simpler!
As root edit the file /etc/pam.d/passwd (add only the lines concerning pam_ldap and leave the others) to read
#%PAM-1.0auth include system-auth
auth sufficient pam_ldap.so
account sufficient pam_ldap.so
account include system-auth
password sufficient pam_ldap.so
password substack system-auth
password optional pam_gnome_keyring.so
Now to change your password Olivier types in the simplest way possible
passwd
This is the result
Enter login(LDAP) password:
New password:
Re-enter new password:
LDAP password information
changed for olivier
passwd: all authentication
tokens updated successfully
That works !!!!
Suggestion for implementation
For the administration I suggest admin4 which can be downloaded here http://www.admin4.org/ we unzip it by typingtar xvfz admin4-3.0.1.tar.gz
this gives the directory admin4-3.0.1 . We will first install the following packages
python-wxpython4
dnspython
python-requests
python-ldap
python3-psycopg2
we go back to the admin4-3.0.1 directory and typepython admin4.py
and here is the result
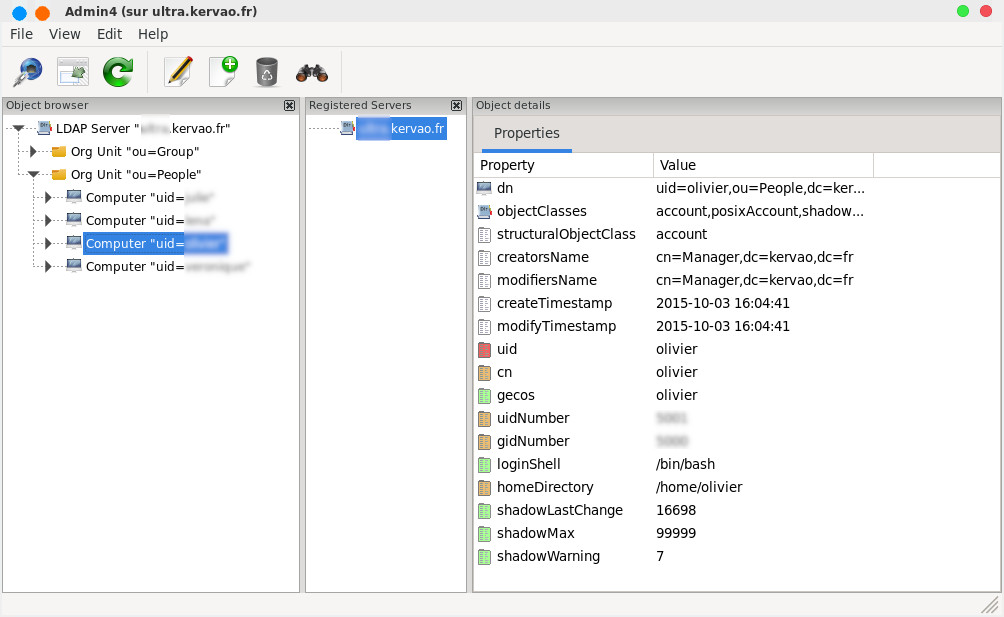
to be more easily accessible I created the script /usr/bin/admin4 containing
#!/bin/bash
python /usr/local/linux/systeme/admin4-3.0.1/admin4.py
by giving it execution rights
chmod 755 /usr/bin/admin4
| [ Back to FUNIX home page ] |
 Welcome
Welcome Linux
Linux Unix
Unix Download
Download